Brute-Forcing from Nmap output

BruteSpray takes nmap GNMAP/XML output and automatically brute-forces services with default credentials using Medusa. BruteSpray can even find non-standard ports by using the -sV inside Nmap.
Installation
Usage
First do an nmap scan with -oG nmap.gnmap or -oX nmap.xml.
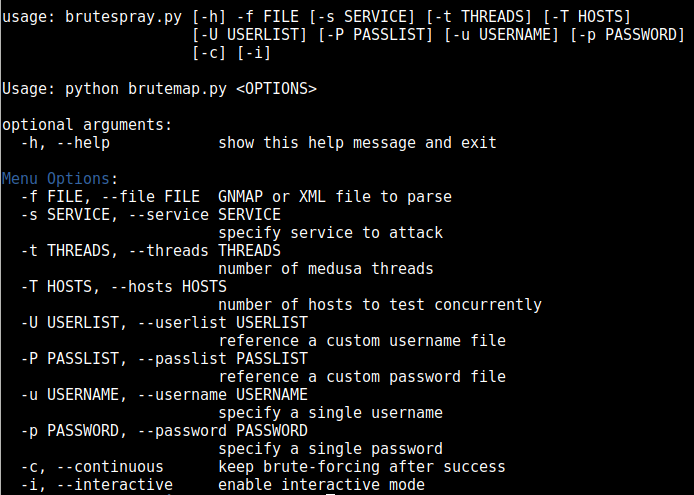
Command: python brutespray.py -h
Command: python brutespray.py -file nmap.gnmap
Command: python brutesrpay.py -file nmap.xml
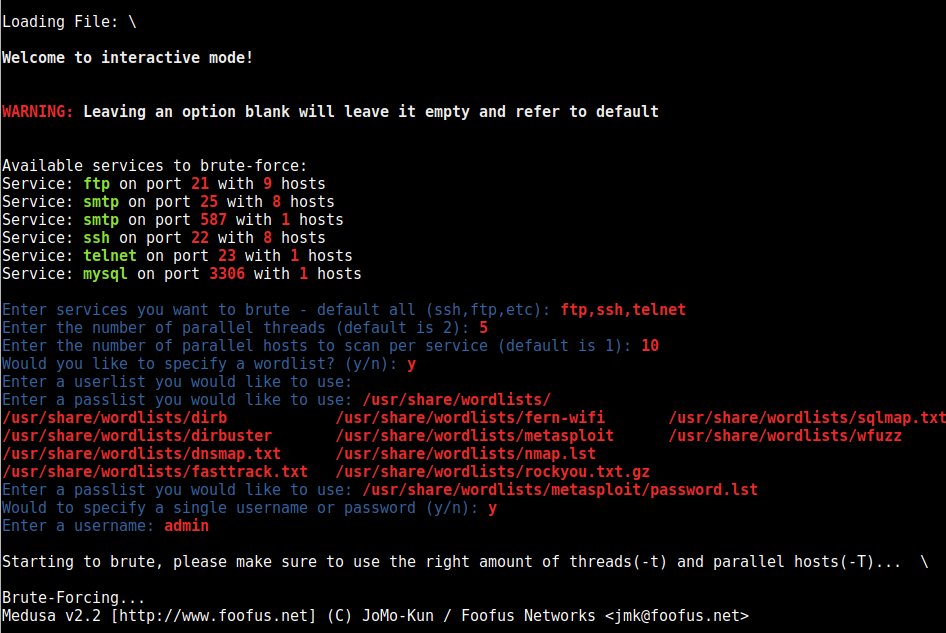
Command: python brutespray.py -file nmap.xml -i
Supported Services
- ssh
- ftp
- telnet
- vnc
- mssql
- mysql
- postgresql
- rsh
- imap
- nntp
- pcanywhere
- pop3
- rexec
- rlogin
- smbnt
- smtp
- svn
- vmauthd
Examples
Using Custom Wordlists:
python brutespray.py -file nmap.gnmap -U /usr/share/wordlist/user.txt -P /usr/share/wordlist/pass.txt -threads 5 -hosts 5
Brute-Forcing Specific Services:
python brutespray.py -file nmap.gnmap -service ftp,ssh,telnet -threads 5 -hosts 5
Specific Credentials:
python brutespray.py -file nmap.gnmap -u admin -p password -threads 5 -hosts 5
Continue After Success:
python brutespray.py -file nmap.gnmap -threads 5 -hosts 5 -c
Use Nmap XML Output
python brutespray.py -file nmap.xml -threads 5 -hosts 5
Interactive Mode
python brutespray.py -file nmap.xml -i
Source: Github
![]()
