
This report has been prepared using depersonalized data processed by Kaspersky Security Network (KSN). The metrics are based on the number of distinct users of Kaspersky Lab products with the KSN feature enabled, who encountered ransomware at least once in a given period, as well as research into the ransomware threat landscape by Kaspersky Lab experts.
This report covers the evolution of the threat from April 2016 to March 2017 and compares it with the period of April 2015 to March 2016.
A brief look at ransomware evolution over a year
The rise of Ransomware-as-a-Service
In May 2016 Kaspersky Lab discovered Petya ransomware that not only encrypts data stored on a computer, but also overwrites the hard disk drive’s master boot record (MBR), leaving infected computers unable to boot into the operating system.
The malware is a notable example of the Ransomware-as-a-Service model, when ransomware creators offer their malicious product ‘on demand’, spreading it by multiple distributors and getting a cut of the profits. In order to get their part of the profit, the Petya authors inserted certain “protection mechanisms” into their malware that do not allow the unauthorized use of Petya samples.
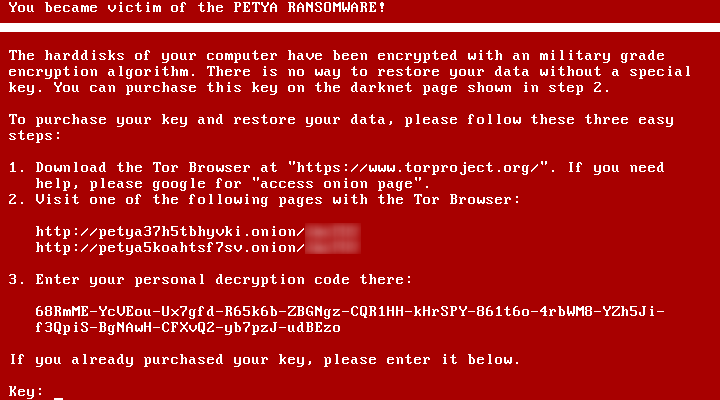
While Ransomware-as-a-Service is not a new trend, this propagation model continues to develop, with more and more ransomware creators offering their malicious product. This approach has proved immensely appealing to criminals who lack the skills, resources or inclination to develop their own malware.
Notable examples of ransomware that appeared in 2016 and used this model were Petya/Mischa and Shark ransomware, which was later rebranded under the name Atom.
The growth of targeted attacks
In early 2017, Kaspersky Lab’s researchers have discovered an emerging and dangerous trend: more and more cybercriminals are turning their attention from attacks against private users to targeted ransomware attacks against businesses.
The attacks are primarily focused on financial organizations worldwide. Kaspersky Lab’s experts have encountered cases where payment demands amounted to over half a million dollars.
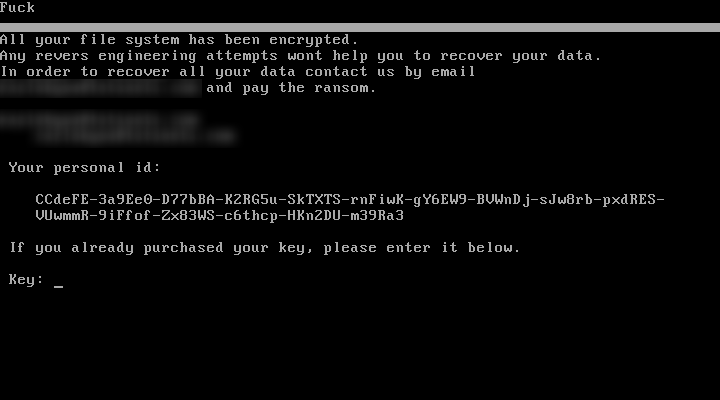
The trend is alarming as ransomware actors start their crusade for new and more profitable victims. There are many more potential ransomware targets in the wild, with attacks resulting in even more disastrous consequences.
The analysis in this report attempts to assess the scale of the problem, and to highlight possible reasons for the new angles of ransomware developments globally.
Main numbers
- The total number of users who encountered ransomware between April 2016 and March 2017 rose by 11.4% compared to the previous 12 months (April 2015 to March 2016) – from 2,315,931 to 2,581,026 users around the world;
- The proportion of users who encountered ransomware at least once out of the total number of users who encountered malware fell by almost 0.8 percentage points, from 4.34% in 2015-2016 to 3.88% in 2016-2017;
- Among those who encountered ransomware, the proportion who encountered cryptors rose by 13.6 percentage points, from 31% in 2015-2016 to 44.6% in 2016-2017;
- The number of users attacked with cryptors rose almost twice, from 718,536 in 2015-2016 to 1,152,299 in 2016-2017;
- The number of users attacked with mobile ransomware fell by 4.62% from 136,532 users in 2015-2016 to 130,232.
Conclusions and predictions
Based on the statistics and trends described in this report, we have come to the following conclusions:
- Ransomware actors are starting to devour each other. This is a sign of growing competition between ransomware gangs.
- The geography statistics show that attackers switch to previously unreached countries, where users are not as well prepared for fighting ransomware, and where competition among criminals is not so high.
- The worrying thing here is the fact that ransomware attacks are becoming increasingly targeted, hitting financial infrastructure across the globe. The reason for the trend is clear – criminals consider targeted ransomware attacks against businesses potentially more profitable than mass attacks against private users.
- The numbers show that ransomware on PCs are still on the rise – albeit at a slower growth rate.
- Moreover, the number of users attacked with mobile ransomware in the observed period fell. This could be a sign of successful collaboration between vendors of security solutions, various law enforcement agencies, and other actors. Increased threat awareness, fueled by global media coverage on the most prominent fraudulent campaigns can also have a part to play.
- Another reason is the development of joint industry efforts to protect users from encryption ransomware.
- Although the statistics show that attacks with ransomware operate on a massive scale, responsibility for most of the mobile attacks rests with just a few groups of malware, most of them spread via affiliate programs. At the same time, PC ransomware shows quite the opposite status, with a lot of malicious actors in the wild conducting ad hoc attacks.
Along with these conclusions we believe that the current ransomware threat landscape provides a good basis for several predictions on how this threat will evolve in the future.
Predictions
- The extortion model is here to stay. More stable growth, which is at a higher level on average, could indicate an alarming trend: a shift from chaotic and sporadic actors’ attempts to gain foothold in threat landscape, to steadier and higher volumes.
- Given the signs of growing competition on the ransomware market, Ransomware-as-a-Service is also becoming more and more popular, attracting new actors.
- Ransomware is growing in sophistication and diversity, offering a lot of ready-to-go solutions to those with fewer skills, resources or time – through a growing and increasingly efficient underground ecosystem.
- Development of criminal-to-criminal infrastructure is fueling the emergence of easy-to-go, ad hoc tools to perform targeted attacks and extort money, making attacks more dispersed. This trend has already taken place and will likely continue in the future.
- Global initiatives which protect users from encryption ransomware will keep gaining momentum.
Fighting back
Through technology: Kaspersky Lab provides a free anti-ransomware tool which is available for all businesses to download and use, regardless of the security solution they have installed.
Through collaboration: The No More Ransom Initiative. On 25 July 2016, the Dutch National Police, Europol, Intel Security and Kaspersky Lab announced the launch of the No More Ransom project – a non-commercial initiative that unites public and private organizations and aims to inform people of the dangers of ransomware and help them to recover their data. The online portal currently carries 50 decryption tools, seven of which were made by Kaspersky Lab. Since the NMR launch, more than 29.000 victims from all over the world have been able to unlock their files for free thanks to Kaspersky Lab tools. The NMR portal is currently available in 14 languages: English, Dutch, French, Italian and Portuguese, German, Spanish, Slovenian, Finnish, Hebrew, Ukrainian, Korean, and Japanese.
![]()
