Virtual attack and defense system
A honeypot is a term used to describe a computer or network setup with the purpose of attracting computer hackers. These computers allow a system administrator or security expert to analyze how a computer hacker may attempt to hack a network without risking the threat to their own network. Any problems discovered while analyzing the honey pot can be implement into the real network or server making it more secure.
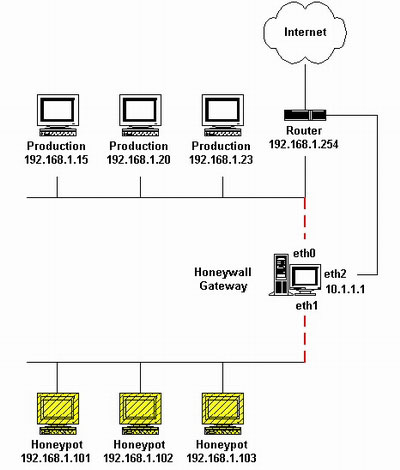
Honeypot is a traditional analogy or some other operating system common general vulnerability , and Honeynet is different, it is a learning tool, here are the two biggest difference between them:
- HoneyPot is to help organizations reduce risks and increase safety organization wide assessment. While the research style is set for getting information from the hacker community.
- Honeynet is a network system, rather than a single host station, the network system is hidden behind a firewall, and all incoming and outgoing data are monitored, captured and controlled. These data can be captured on our research and analysis tools are used by the intruder, methods and motives. In this Honeynet, we can use a variety of different operating
systems and devices, such as the Solaris the Linux the Windows NT the Cisco of Switch and so on. Thus created network
environment will look more authentic, but we have a different system platforms to run on top of a different service than
as a Linux DNS server, Windows’s webserver or a Solaris Server of the FTP, we can learn different tools and different strategies – and perhaps some of the intruder only to aim at several specific on the loopholes in the system, and this diversity of our system, the more likely reveal some of their characteristics. Honeynet is a tool for hackers to learn how to invade the system, including the design of a good network system.
The most common Honeynet build elements are:
Firewall, which records all incoming and outgoing connections and provides NAT services and DOS protection. IDS and firewalls are sometimes placed in the same position, it records the traffic on the web and look for clues attacks and intrusions. Remote log computer, a slight modification to all of the intruder’s instructions can be sent to the system log. System logs are usually set to a distal end of the system log. Ưe set a good Honeypot can be any operating system, when setting the Honeypot, can do little to change in order to avoid an intruder perceptible that this is a Honeynet.
Honeynet is a valuable research, learning and educational tools through the tool so that we can understand the intruder attacks, so the future can detect intrusion. Analysis of monitoring information and can be collected from the Honeynet depending attack trend. This information can also be used to teach education and training.
In general, there are two main reasons for building a HoneyPot:
- Learn how to detect intruders and attempt to gain access to the system, when the hacker’s actions are recorded, we
can take this analysis, to find better ways to protect our real system. - In the case of evidence necessary for the arrest of an intruder, such information is required in court to serve as evidence against the intruder.
Advantages and Disadvantages of HoneyPot
Advantage:
1. Data collection
Honeypots collect a small amount of data, but the data are of high value. It removes a lot of noise, so that it can be
simple enough to gather information. One of the best in security issues in, that is how a lot of information on them, to find
the information you need, HoneyPot enables you to quickly and easily gather information and understanding. For example
HoneyNet Project, which is a research honeypot team, flat collapse 1-5MB information collected every day,
these are generally very valuable information, not only to see the action on the web, and can learn how the intruder invaded
this system.
2. Resources
Many security tools are limited by bandwidth. Network intrusion detection devices are not able to track the behavior of all of the network, and
discards the packet. Centralized log servers do not collect all of the system logs, potentially losing log records.
Honeypots does not have this problem, it just to intercept the action for his relationship.
Disadvantages:
1. Single data collection point
HoneyPots placed a big loopholes in the system, if not to attack the attacker, which became completely no value , can not know any unauthorized action.
2. Risks
HoneyPots for your environment can lead to the risk of an attack as the attacker additional platform is becoming the risk of mobility, all rely on how to build and how to use Honeypots.
![]()


