Nightcall
Automated enumeration script built to reduce repetitive tasks during large network pentests. Initial host discovery performed by basic throttled masscan, followed by service enumeration of each host, full port if host count less than a preconfigured constant, top port count otherwise. Nmap outputs are then parsed and common tooling queued up for follow up enumeration based on discovered service. All tasks after initial host discovery are multi-processed, with the task count being a configurable constant.
While actions and tooling are by no means exhaustive, tooling and configuration are meant to be easily configurable and modifiable to suit testers’ needs. Most command configuration strings and wordlist selections are located at the beginning of the script. Nmap NSEs were selected for speed, safety, and usefulness. Nightcall is not meant as a replacement for vulnerability scanning solutions such as Tenable or OpenVAS, merely to fill a gap where manual testing efforts intersect. Additionally, Nightcall is focused more on understanding known IP ranges than the discovery of unknown subdomains. CaKinney’s domained is a good option for that task.
Tooling
- masscan – host discovery amongst sparse ranges, throttled to reduce impact potential
- nmap – service enumeration and select NSEs
- whatweb – web technology identification
- cutycapt – Image capture
- enum4linux – smb/samba enumeration
- dnsrecon – general dns zone xfer and ptr review
- metasploit – additional auxiliary checks
Optional Web Checks
- nikto – general web service enumeration
- wfuzz – predictable content discovery
- wafw00f – IDS / WAF detection
- wpscan – wordpress enumeration
- joomscan – joomla enumeration
Optional Brute-Forcing
- medusa – optional brute-forcing attempts
Auxiliary MSF Modules
- auxiliary/scanner/http/dir_listing
- auxiliary/scanner/http/http_put
- auxiliary/scanner/http/host_header_injection
- auxiliary/scanner/http/smt_ipmi_49152_exposure
- auxiliary/scanner/ipmi/ipmi_cipher_zero
- auxiliary/scanner/ipmi/ipmi_dumphashes
- auxiliary/scanner/ipmi/ipmi_version
- auxiliary/scanner/misc/java_rmi_server
- auxiliary/scanner/smtp/smtp_enum
- auxiliary/scanner/snmp/snmp_login
- auxiliary/scanner/ssh/ssh_enumusers
- auxiliary/scanner/ssl/openssl_ccs
- auxiliary/scanner/http/crawler (optional web)
- auxiliary/scanner/http/jboss_vulnscan (optional web)
- auxiliary/scanner/http/tomcat_mgr_login (optional web)
- auxiliary/scanner/tftp/tftpbrute (optional brute)
Output
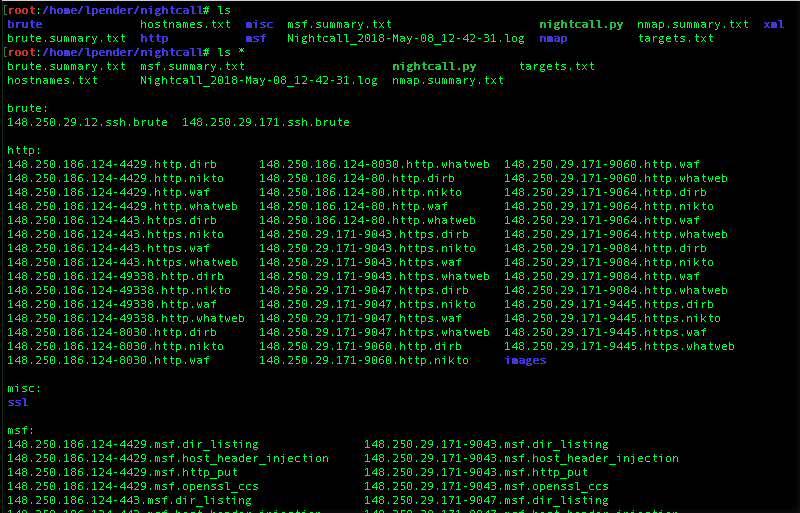
Tooling output will be collected and organized into the following subdirectories during enumeration by {host}-{port}.{type}, where type is some combination of categorization and tool depending on the application.
- nmap – textual and greppable nmap output
- xml – masscan and nmap xml
- msf – metasploit module results
- misc – various tooling output
- http – web related output
- http/images – screenshot captures
- brute – brute-forcing results if selected
This approach was preferred over a by-host-subfolder strategy due to the massive amount of directories that can be created and ease of grepping. Some minor summarization will be collected from specific files. A primary log file in the project directory contains a journal of commands executed and their associated timestamps.
Use
root@kali:~# python3 nightcall.py
usage: nightcall.py [-h] [-sP] [-i IFACE] [-f TARGET_FILE] [--install-prereqs]
[-b] [-w] [--disable-resolve]
[single_address]
positional arguments:
single_address single host or network (excludes -f)
optional arguments:
-h, --help show this help message and exit
-sP, --skip-portscans
skip portscans, directly import xml
-i IFACE, --iface IFACE
interface to use for masscan and nmap
-f TARGET_FILE, --target-file TARGET_FILE
target file containing line separated ip addresses
(cidr supported)
--install-prereqs attempt to install TQDM progress bar, python3-pip,
masscan, nfs-common, xvfb
-b, --brute enable bruteforcing (consider lockouts)
-w, --web enable additional web related scans
--disable-resolve disable separate hostname resolution (outside nmap)Download
git clone https://github.com/walmartlabs/nightcall.git
apt-get install python3-pip masscan nfs-common xvfb -yqq
pip3 install tqdm
Copyright (c) 2017-present, Walmart Inc.
Source: https://github.com/walmartlabs/
![]()
