Bypass Antivirus & Exploit Windows Using PowerShell

Affected Version
- Microsoft Windows 10 Version 1607 for 32-bit Systems
- Microsoft Windows 10 Version 1607 for x64-based Systems
- Microsoft Windows 10 for 32-bit Systems
- Microsoft Windows 10 for x64-based Systems
- Microsoft Windows 10 version 1511 for 32-bit Systems
- Microsoft Windows 10 version 1511 for x64-based Systems
- Microsoft Windows 10 version 1703 for 32-bit Systems
- Microsoft Windows 10 version 1703 for x64-based Systems
- Microsoft Windows 7 for 32-bit Systems SP1
- Microsoft Windows 7 for x64-based Systems SP1
- Microsoft Windows 8.1 for 32-bit Systems
- Microsoft Windows 8.1 for x64-based Systems
- Microsoft Windows RT 8.1
- Microsoft Windows Server 2008 R2 for Itanium-based Systems SP1
- Microsoft Windows Server 2008 R2 for x64-based Systems SP1
- Microsoft Windows Server 2008 for 32-bit Systems SP2
- Microsoft Windows Server 2008 for Itanium-based Systems SP2
- Microsoft Windows Server 2008 for x64-based Systems SP2
- Microsoft Windows Server 2012
- Microsoft Windows Server 2012 R2
- Microsoft Windows Server 2016
How to using CVE-2017-8464 to exploit Windows.
- Generate payload using metasploit
- Copy root.ps1 to /var/www/html
3. Create powershell script
Or you can create powershell shortcut to download and execute remote code using System.Net.WebClient.DownloadString(uri address) method
4. Put this powershell script to network sharing folder
5. Start msfconsole

6. The virus scanning result
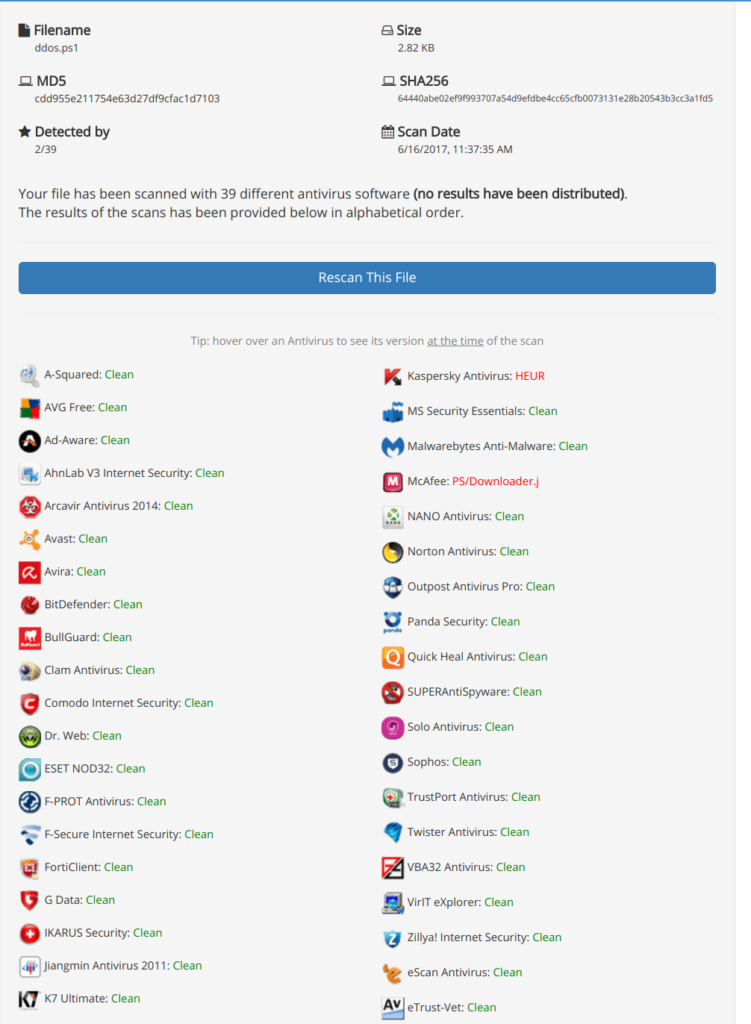
7. Your victim click to run powershell script… You will get command shell
![]()
