Web Vulnerability Scan (WMAP)
Introduce
The Metasploit Project is a computer security project that provides information about security vulnerabilities and aids in penetration testing and IDS signature development. Its best-known sub-project is the open source[2] Metasploit Framework, a tool for developing and executing exploit code against a remote target machine. Other important sub-projects include the Opcode Database, shellcode archive and related research. The Metasploit Project is well known for its anti-forensic and evasion tools, some of which are built into the Metasploit Framework. On this post, i will talk about wmap which can be loaded in Metasploit.
Wmap is a tool derived from SQLMap and can perform vulnerability checks on Web applications in a similar fashion. Metasploit is also supported as a module type, and it can be used strongly by connecting host and vulnerability information with each other.
Using WMAP in Metasploit
On msfconsole, load wmap via the load command.
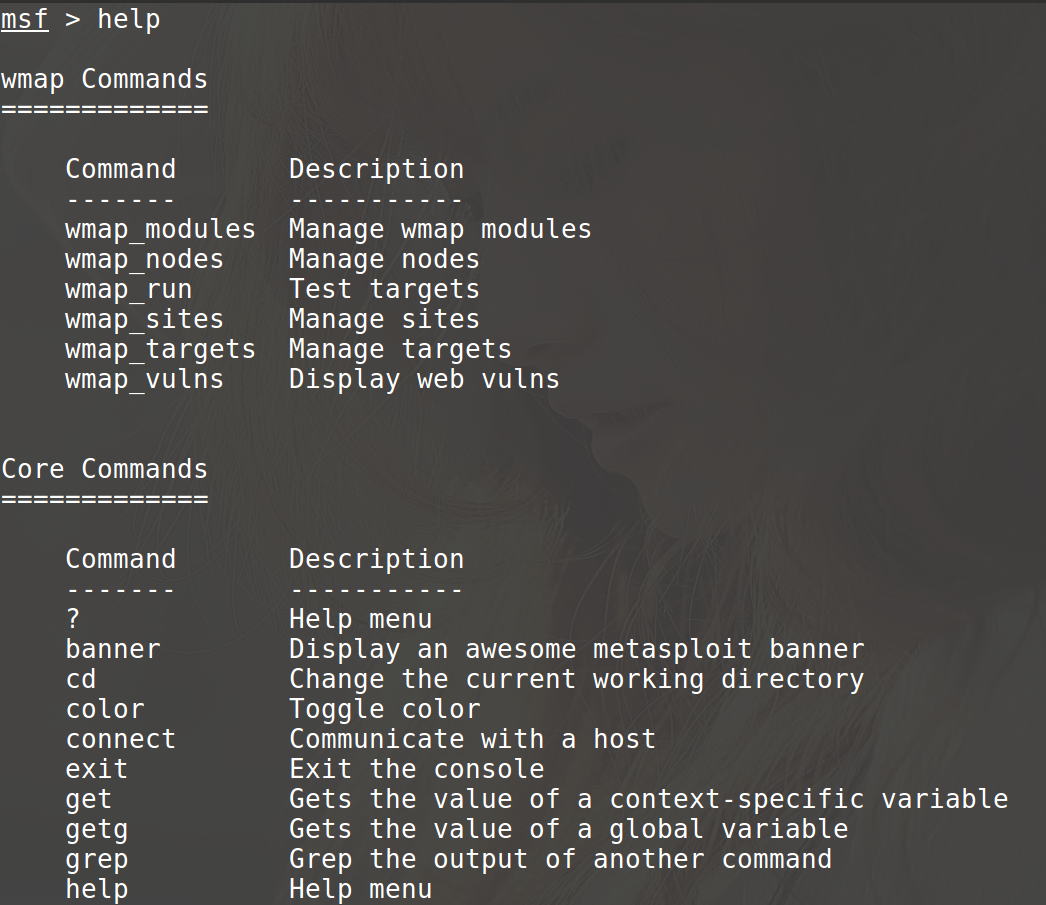
Use help command for viewing all command on this plugin
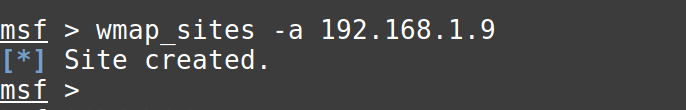
Specify the target site using the -a option of wmap_sites.
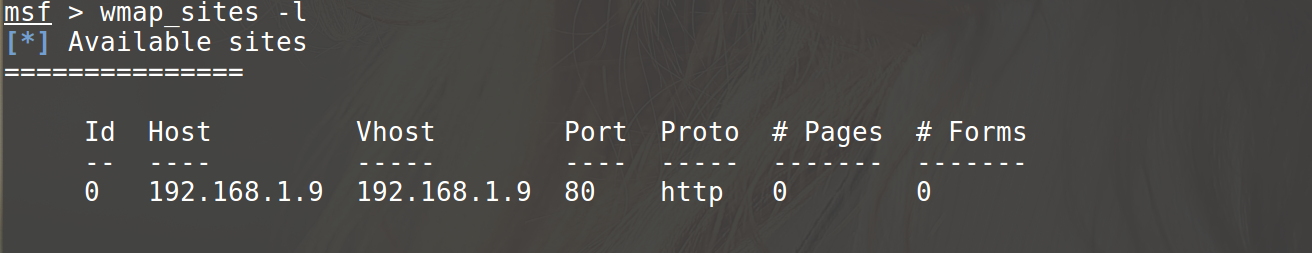
After specifying the list, the list of target sites created when checking the list is checked with the -l option.
The remote system is scanned with the -t option, which allows simple testing before actual execution.
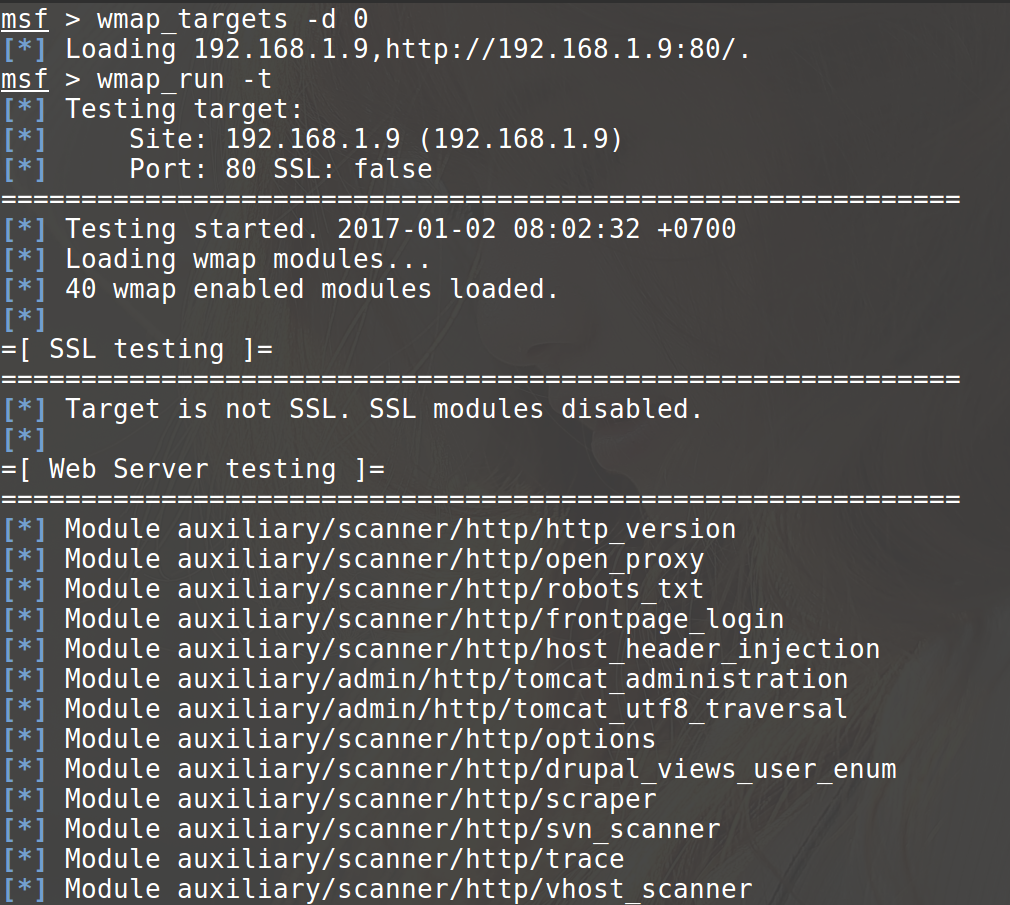
Testing is possible via the -e option.
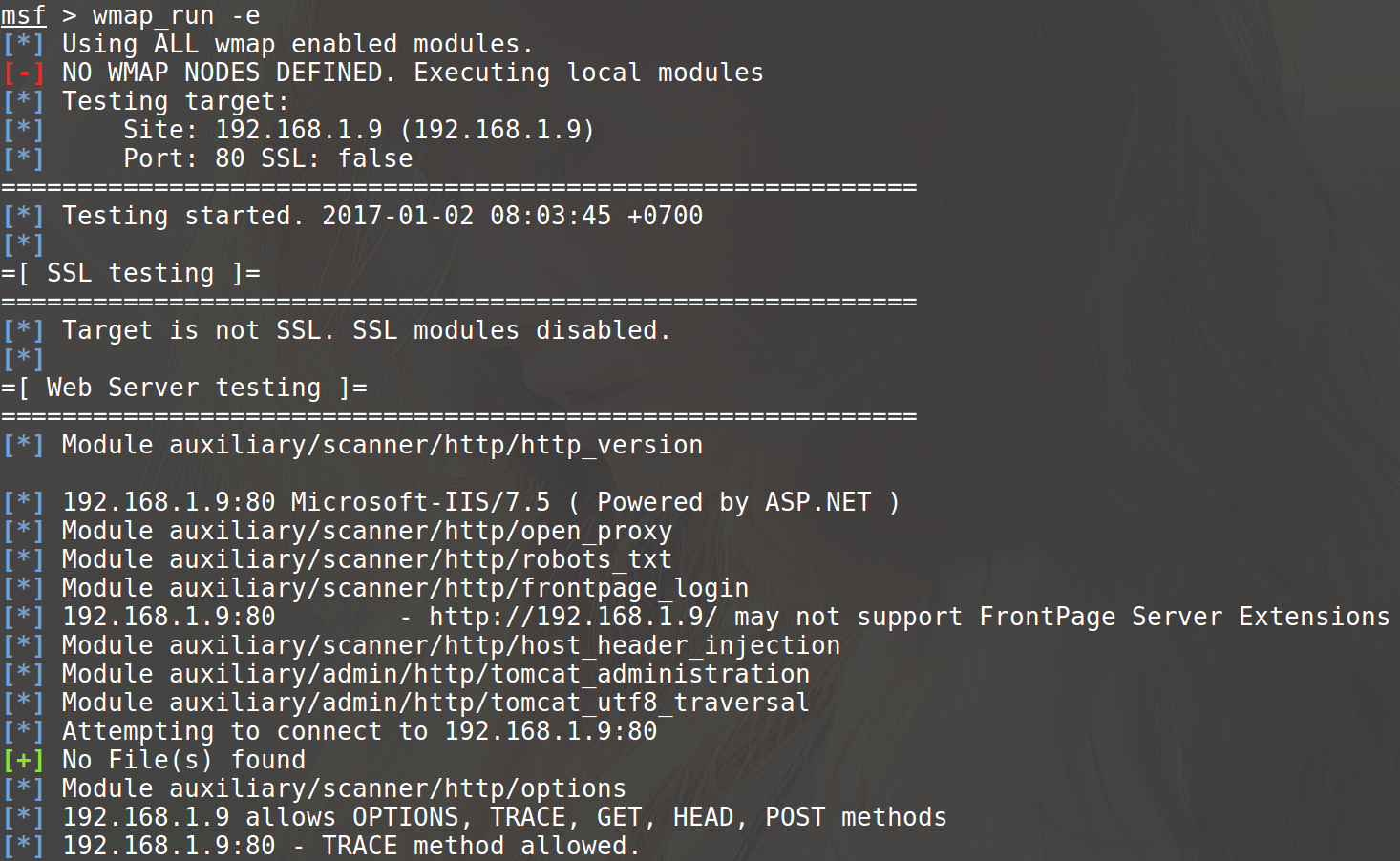
Any vulnerability found through wmap is stored in metasploit db and can be verified through the vulns command.
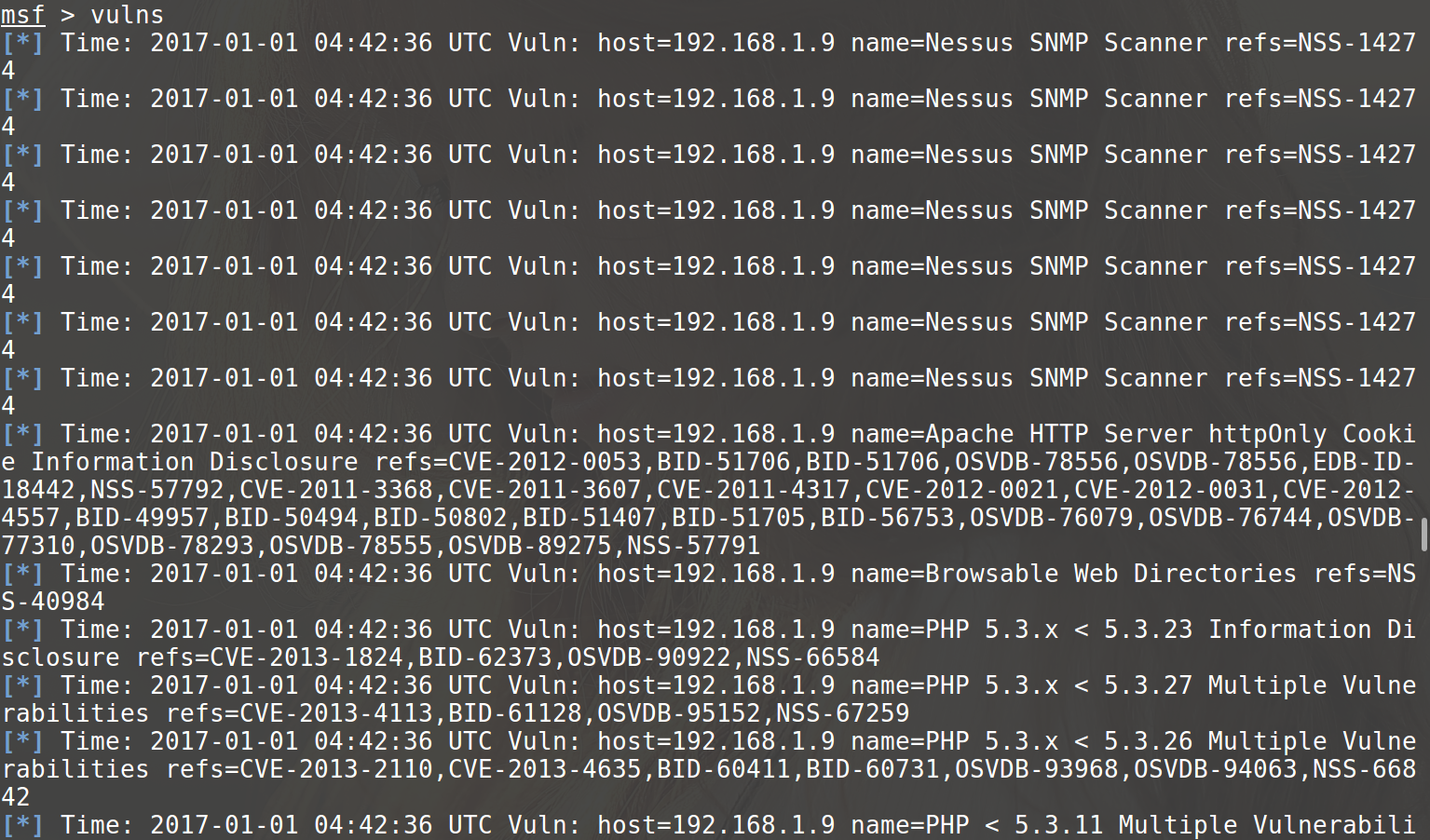
![]()

