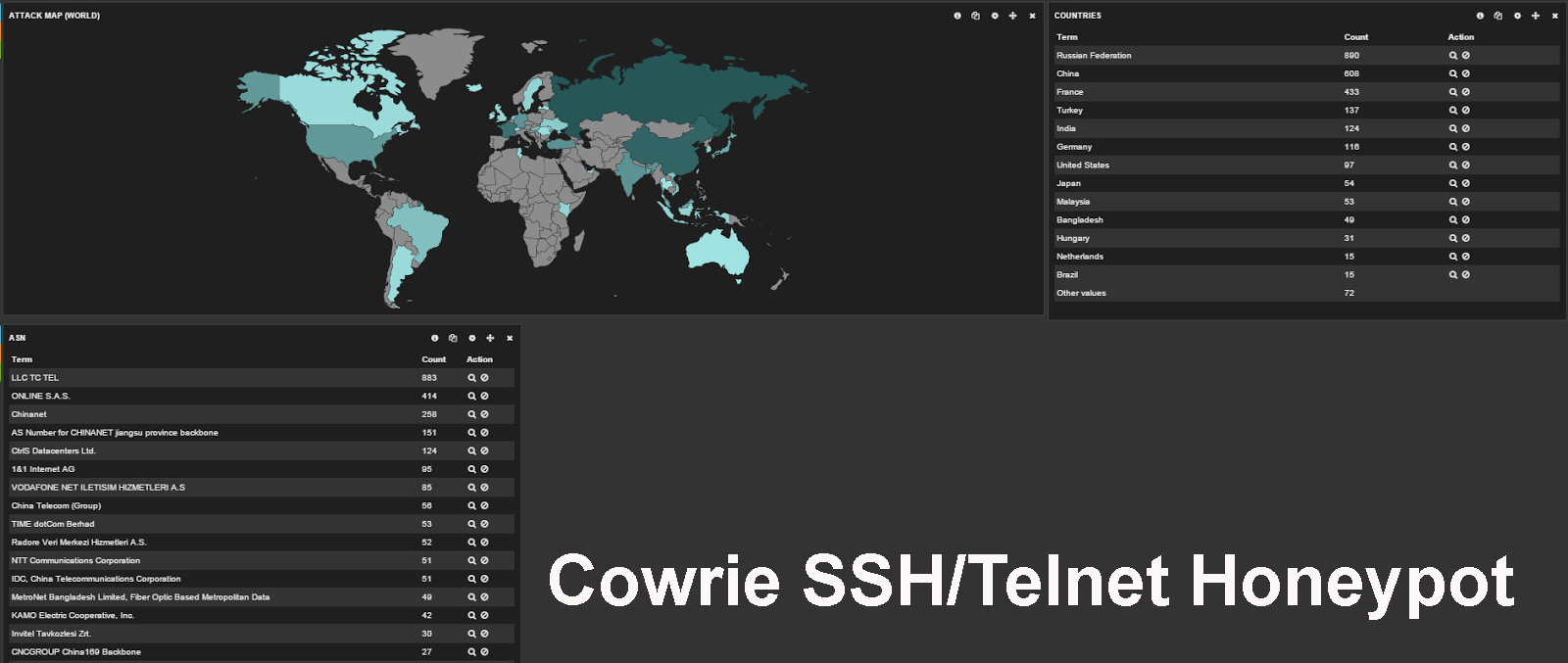
Cowrie
SSH/Telnet Honeypot
Cowrie is a medium interaction SSH and Telnet honeypot designed to log brute force attacks and the shell interaction performed by the attacker.
Cowrie is developed by Michel Oosterhof
Features
Some interesting features:
- Fake filesystem with the ability to add/remove files. A full fake filesystem resembling a Debian 5.0 installation is included
- Possibility of adding fake file contents so the attacker can
catfiles such as/etc/passwd. Only minimal file contents are included - Session logs stored in an UML Compatible format for easy replay with original timings
- Cowrie saves files downloaded with wget/curl or uploaded with SFTP and scp for later inspection
Additional functionality over standard kippo:
- SFTP and SCP support for file upload
- Support for SSH exec commands
- Logging of direct-tcp connection attempts (ssh proxying)
- Forward SMTP connections to SMTP Honeypot (e.g. mailoney)
- Logging in JSON format for easy processing in log management solutions
- Many, many additional commands
Requirements
Software required:
- Python 2.7+, (Python 3 not yet supported due to Twisted dependencies)
- python-virtualenv
For Python dependencies, see requirements.txt
Files of interest:
cowrie.cfg– Cowrie’s configuration file. Default values can be found incowrie.cfg.distdata/fs.pickle– fake filesystemdata/userdb.txt– credentials allowed or disallowed to access the honeypotdl/– files transferred from the attacker to the honeypot are stored herehoneyfs/– file contents for the fake filesystem – feel free to copy a real system here or usebin/fsctllog/cowrie.json– transaction output in JSON formatlog/cowrie.log– log/debug outputlog/tty/*.log– session logstxtcmds/– file contents for the fake commandsbin/createfs– used to create the fake filesystembin/playlog– utility to replay session logs
Read more.
Download
![]()