Microsoft Malware Protection Engine Remote Code Execution Vulnerability (CVE-2017-0290)
Vulnerability identify
CVE-2017-0290
Vulnerability Finder
Natalie Silvanovich and Tavis Ormandy of Google Project Zero
Vulnerability
A brief description of the vulnerability
A remote code execution vulnerability is triggered when the Microsoft Malware Protection Engine does not properly scan an attacker’s well-crafted file that causes memory corruption. An attacker who successfully exploited this vulnerability could execute arbitrary code under the LocalSystem account and control the system. An attacker can install a program; view, change, or delete data; even create a new account with full user rights.
To exploit this vulnerability, the specially crafted files must be scanned by the affected Microsoft Malware Protection Engine. An attacker can place a specially crafted file in a location that is scanned by the Microsoft Malware Protection Engine in a number of ways. For example, an attacker could use a website to send a specially crafted file to the victim’s system, which is scanned by the Microsoft Malware Protection Engine when the user views the site. An attacker could also scan a specially crafted file in an Instant Messenger message by e-mail or when opening a file. In addition, an attacker can upload a specially crafted file to a managed server by using a Web site that provides hosted user content, and the Microsoft Malware Protection Engine scans the specially crafted files provided by the attacker on the managed server.
If real-time protection is enabled for the affected anti-malware, the Microsoft Malware Protection Engine will automatically scan the file to exploit the vulnerability when scanning a specially crafted file. If real-time scanning is not enabled, the attacker will have to wait until a scheduled scan occurs to exploit the vulnerability.
Affected software
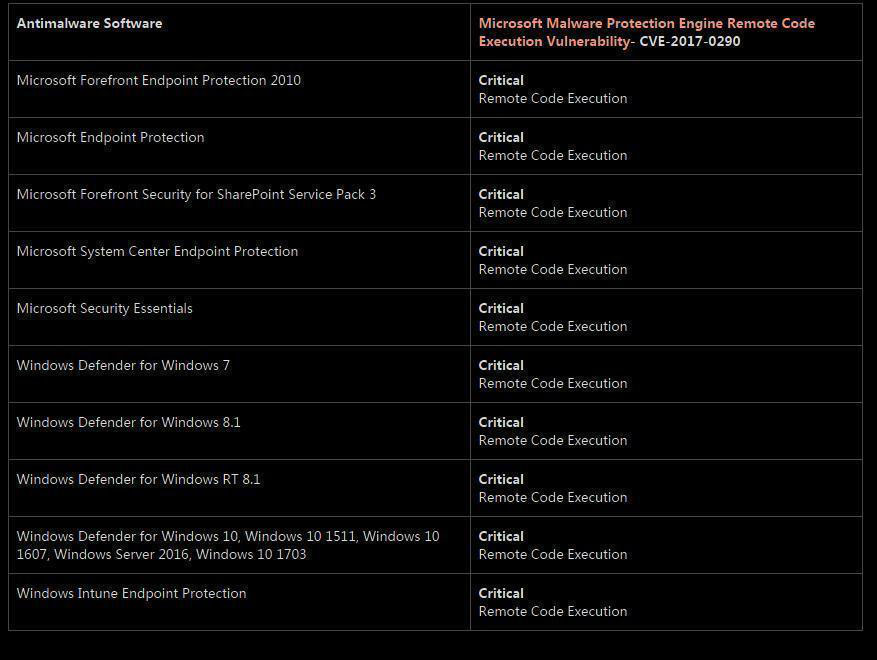
Exploitation
https://www.exploit-db.com/exploits/41975/
Fix suggestions
Check if the update is installed, and for the affected software, verify that the Microsoft Malware Protection Engine version is 1.1.10701.0 or later.
If necessary, install the update. The administrator of the enterprise anti-malware deployment should ensure that its update management software is configured for automatic updates and deployments that will take effect within 48 hours. For more information about how to manually update the Microsoft Malware Protection Engine and Malware definitions, see Microsoft Knowledge Base article 2510781
More Vulnerability Details:
https://bugs.chromium.org/p/project-zero/issues/detail?id=1252&desc=5
Reference link
https://technet.microsoft.com/en-us/library/security/4022344
https://bugs.chromium.org/p/project-zero/issues/detail?id=1252&desc=5
![]()

