Testing TLS/SSL encryption anywhere on any port
testssl.sh is a free command line tool which checks a server’s service on any port for the support of TLS/SSLcyphers, protocols as well as some cryptographic flaws.
Key features
- Clear output: you can tell easily whether anything is good or bad
- Ease of installation: It works for Linux, Darwin, FreeBSD, NetBSD and MSYS2/Cygwin out of the box: no need to install or configure something, no gems, CPAN, pip or the like.
- Flexibility: You can test any SSL/TLS enabled and STARTTLS service, not only web servers at port 443
- Toolbox: Several command line options help you to run YOUR test and configure YOUR output
- Reliability: features are tested thoroughly
- Verbosity: If a particular check cannot be performed because of a missing capability on your client side, you’ll get a warning
- Privacy: It’s only you who sees the result, not a third party
- Freedom: It’s 100% open source. You can look at the code, see what’s going on and you can change it.
- Heck, even the development is open (github)
testssl.sh URI as the default invocation does the so-called default run which does a number of checks and puts out the results colourized (ANSI and termcap) on the screen. It does every check listed below except -E which are (order of appearance):
- displays a banner (see below), does a DNS lookup also for further IP addresses and does for the returned IP address a reverse lookup. Last but not least a service check is being done.
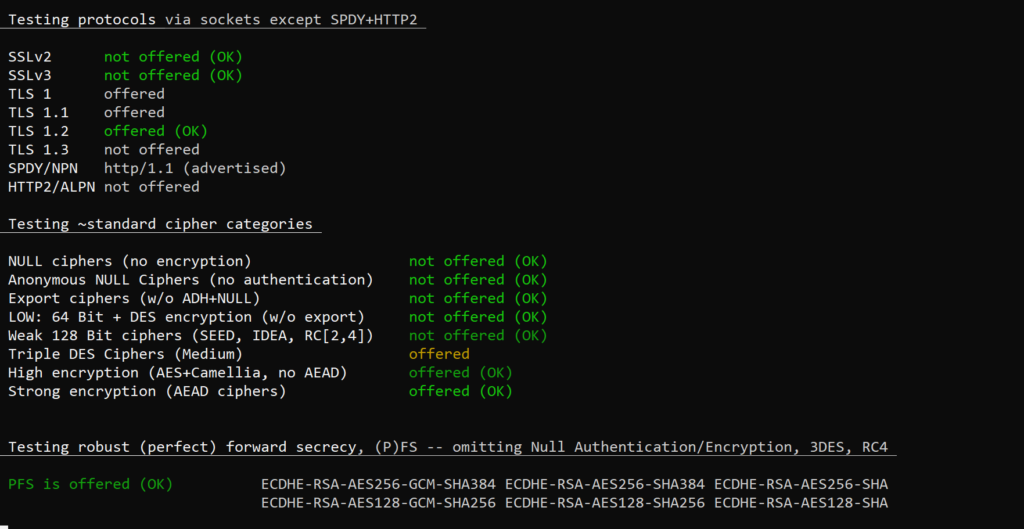
- SSL/TLS protocol check
- standard cipher categories to give you upfront an idea for the ciphers supported
- checks (perfect) forward secrecy: ciphers and elliptical curves
- server preferences (server order)
- server defaults (certificate info, TLS extensions, session information)
- HTTP header (if HTTP detected or being forced via
--assume-http) - vulnerabilities
- testing each of 359 ciphers
- client simulation
Changelog v3.0 rc5
This is the fifth release candidate of testssl.sh 3.0 to reflect changes. All distributors and others who use it also for production-like environment are encouraged to switch to this branch as 2.9.5 won’t be supported anymore once 3.0 has been released: Bug fixing will take place here only.
We take robustness seriously. This release contains bug fixes mostly.
For all changes, use git log. Excerpt:
- Modernized client handshakes
- Further code sanitizing
- Fixes in CSV files and JSON files creation and some ACE loadbalancer related improvements
- Fix session tickets and resumption
- OpenSSL 1.1.1 fixes
- Darwin OpenSSL binary
- Updated certificate store
- Add SSLv2 to SWEET
Download
git clone –depth 1 https://github.com/drwetter/testssl.sh.git
Usage
./testssl.sh
"testssl.sh [options] <URI>" or "testssl.sh <options>"
"testssl.sh <options>", where <options> is:
--help what you're looking at
-b, --banner displays banner + version of testssl.sh
-v, --version same as previous
-V, --local pretty print all local ciphers
-V, --local <pattern> which local ciphers with <pattern> are available? If pattern is not a number: word match
<pattern> is always an ignore case word pattern of cipher hexcode or any other string in the name, kx or bits
"testssl.sh <URI>", where <URI> is:
<URI> host|host:port|URL|URL:port port 443 is default, URL can only contain HTTPS protocol)
"testssl.sh [options] <URI>", where [options] is:
-t, --starttls <protocol> Does a default run against a STARTTLS enabled <protocol,
protocol is <ftp|smtp|pop3|imap|xmpp|telnet|ldap|postgres|mysql> (latter 4 require supplied openssl)
--xmpphost <to_domain> For STARTTLS enabled XMPP it supplies the XML stream to-'' domain -- sometimes needed
--mx <domain/host> Tests MX records from high to low priority (STARTTLS, port 25)
--file <fname|fname.gnmap> Mass testing option: Reads command lines from <fname>, one line per instance.
Comments via # allowed, EOF signals end of <fname>. Implicitly turns on "--warnings batch".
Alternatively: nmap output in greppable format (-oG) (1x port per line allowed)
--mode <serial|parallel> Mass testing to be done serial (default) or parallel (--parallel is shortcut for the latter)
single check as <options> ("testssl.sh URI" does everything except -E and -g):
-e, --each-cipher checks each local cipher remotely
-E, --cipher-per-proto checks those per protocol
-s, --std, --standard tests certain lists of cipher suites by strength
-p, --protocols checks TLS/SSL protocols (including SPDY/HTTP2)
-S, --server-defaults displays the server's default picks and certificate info
-P, --server-preference displays the server's picks: protocol+cipher
-x, --single-cipher <pattern> tests matched <pattern> of ciphers
(if <pattern> not a number: word match)
-c, --client-simulation test client simulations, see which client negotiates with cipher and protocol
-h, --header, --headers tests HSTS, HPKP, server/app banner, security headers, cookie, reverse proxy, IPv4 address
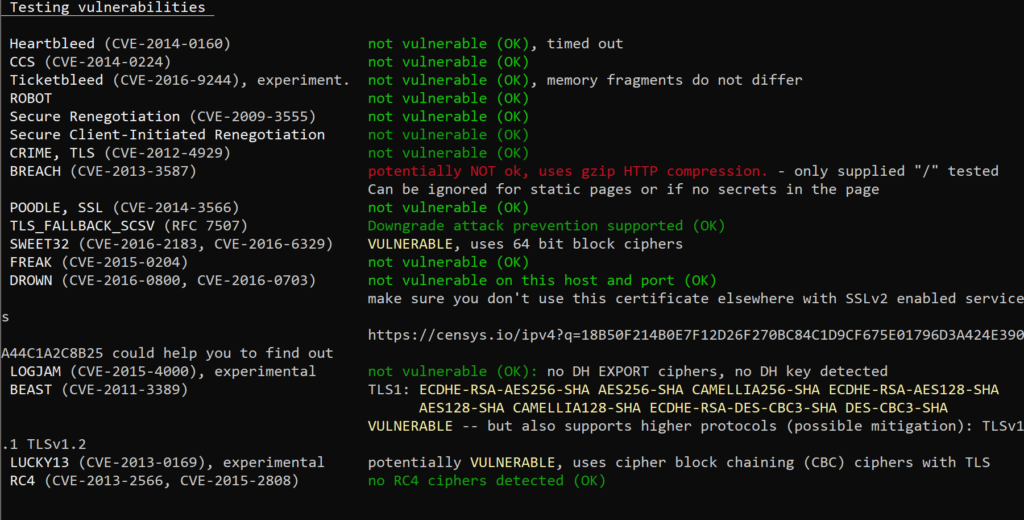
-U, --vulnerable tests all (of the following) vulnerabilities (if applicable)
-H, --heartbleed tests for Heartbleed vulnerability
-I, --ccs, --ccs-injection tests for CCS injection vulnerability
-T, --ticketbleed tests for Ticketbleed vulnerability in BigIP loadbalancers
-BB, --robot tests for Return of Bleichenbacher's Oracle Threat (ROBOT) vulnerability
-R, --renegotiation tests for renegotiation vulnerabilities
-C, --compression, --crime tests for CRIME vulnerability (TLS compression issue)
-B, --breach tests for BREACH vulnerability (HTTP compression issue)
-O, --poodle tests for POODLE (SSL) vulnerability
-Z, --tls-fallback checks TLS_FALLBACK_SCSV mitigation
-W, --sweet32 tests 64 bit block ciphers (3DES, RC2 and IDEA): SWEET32 vulnerability
-A, --beast tests for BEAST vulnerability
-L, --lucky13 tests for LUCKY13
-F, --freak tests for FREAK vulnerability
-J, --logjam tests for LOGJAM vulnerability
-D, --drown tests for DROWN vulnerability
-f, --pfs, --fs, --nsa checks (perfect) forward secrecy settings
-4, --rc4, --appelbaum which RC4 ciphers are being offered?
-g, --grease tests several server implementation bugs like GREASE and size limitations
-9, --full includes tests for implementation bugs and cipher per protocol (could disappear)
tuning / connect options (most also can be preset via environment variables):
--fast omits some checks: using openssl for all ciphers (-e), show only first
preferred cipher.
--bugs enables the "-bugs" option of s_client, needed e.g. for some buggy F5s
--assume-http if protocol check fails it assumes HTTP protocol and enforces HTTP checks
--ssl-native fallback to checks with OpenSSL where sockets are normally used
--openssl <PATH> use this openssl binary (default: look in $PATH, $RUN_DIR of testssl.sh)
--proxy <host:port|auto> connect via the specified HTTP proxy, auto: autodetermination from $env ($http(s)_proxy)
-6 also use IPv6. Works only with supporting OpenSSL version and IPv6 connectivity
--ip <ip> a) tests the supplied <ip> v4 or v6 address instead of resolving host(s) in URI
b) arg "one" means: just test the first DNS returns (useful for multiple IPs)
-n, --nodns do not try any DNS lookup
--sneaky leave less traces in target logs: user agent, referer
output options (can also be preset via environment variables):
--warnings <batch|off|false> "batch" doesn't wait for keypress, "off" or "false" skips connection warning
--openssl-timeout <seconds> useful to avoid hangers. <seconds> to wait before openssl connect will be terminated
--quiet don't output the banner. By doing this you acknowledge usage terms normally appearing in the banner
--wide wide output for tests like RC4, BEAST. PFS also with hexcode, kx, strength, RFC name
--show-each for wide outputs: display all ciphers tested -- not only succeeded ones
--mapping <openssl| openssl: use the OpenSSL cipher suite name as the primary name cipher suite name form (default)
rfc| rfc: use the RFC cipher suite name as the primary name cipher suite name form
no-openssl| no-openssl: don't display the OpenSSL cipher suite name, display RFC names only
no-rfc> no-rfc: don't display the RFC cipher suite name, display OpenSSL names only
--color <0|1|2|3> 0: no escape or other codes, 1: b/w escape codes, 2: color (default), 3: extra color (color all ciphers)
--colorblind swap green and blue in the output
--debug <0-6> 1: screen output normal but keeps debug output in /tmp/. 2-6: see "grep -A 5 '^DEBUG=' testssl.sh"
file output options (can also be preset via environment variables)
--log, --logging logs stdout to '${NODE}-p${port}${YYYYMMDD-HHMM}.log' in current working directory (cwd)
--logfile|-oL <logfile> logs stdout to 'dir/${NODE}-p${port}${YYYYMMDD-HHMM}.log'. If 'logfile' is a dir or to a specified 'logfile'
--json additional output of findings to flat JSON file '${NODE}-p${port}${YYYYMMDD-HHMM}.json' in cwd
--jsonfile|-oj <jsonfile> additional output to the specified flat JSON file or directory, similar to --logfile
--json-pretty additional JSON structured output of findings to a file '${NODE}-p${port}${YYYYMMDD-HHMM}.json' in cwd
--jsonfile-pretty|-oJ <jsonfile> additional JSON structured output to the specified file or directory, similar to --logfile
--csv additional output of findings to CSV file '${NODE}-p${port}${YYYYMMDD-HHMM}.csv' in cwd or directory
--csvfile|-oC <csvfile> additional output as CSV to the specified file or directory, similar to --logfile
--html additional output as HTML to file '${NODE}-p${port}${YYYYMMDD-HHMM}.html'
--htmlfile|-oH <htmlfile> additional output as HTML to the specifed file or directory, similar to --logfile
--out(f,F)ile|-oa/-oA <fname> log to a LOG,JSON,CSV,HTML file (see nmap). -oA/-oa: pretty/flat JSON. "auto" uses '${NODE}-p${port}${YYYYMMDD-HHMM}'
--hints additional hints to findings
--severity <severity> severities with lower level will be filtered for CSV+JSON, possible values <LOW|MEDIUM|HIGH|CRITICAL>
--append if (non-empty) <logfile>, <csvfile>, <jsonfile> or <htmlfile> exists, append to file. Omits any header
--outprefix <fname_prefix> before '${NODE}.' above prepend <fname_prefix>
Options requiring a value can also be called with '=' e.g. testssl.sh -t=smtp --wide --openssl=/usr/bin/openssl <URI>.
<URI> always needs to be the last parameter.
Copyright (C) 2014 drwetter
Source: https://github.com/drwetter/
![]()
