Exploiting Apache Struts S2-045 (CVE-2017-5638) vulnerability
Apache Struts is an open source project maintained by the Apache Software Foundation, an open source MVC framework for creating enterprise Java Web applications, offering two versions of the framework products: Struts 1 and Struts 2. Struts2 is a MVC design based on the Web application framework, which is essentially equivalent to a servlet, in the MVC design pattern, Struts2 as a controller (Controller) to establish the model and view data interaction. Struts 2 is the next generation of Struts products, is in the struts 1 and WebWork technology based on the merger of the new Struts 2 framework.
Apache Struts 2.3.5 – 2.3.31 and 2.5 – 2.5.10 versions exist for remote code execution vulnerabilities (CVE-2017-5638). The vulnerability is due to the exception function of the upload function that does not correctly handle the user input error message. Causing a remote attacker to use the vulnerability to send arbitrary commands on the affected server by sending a malicious packet.
The principle of loopholes
- based on the Jakarta (Jakarta Multipart parser) plug-in file upload function
- malicious attackers carefully constructed Content-Type value
- through the version alignment positioning loopholes
Vulnerability and repair measures
An attacker can exploit this vulnerability by sending a maliciously crafted HTTP packet, execute a system command on the affected server, and further control the server completely, resulting in denial of service, data leakage, and site tampering. Because the vulnerability exploits without any preconditions (such as opening dmi, debug and other functions) and the opening of any plug-ins, so the vulnerability is more serious.
Affected users can upgrade to Apache Struts 2.3.32 or Apache Struts 2.5.10.1 to eliminate the vulnerability.
S2-045 exploit code module
Metasploit has a lot of system vulnerabilities using code, but it does not have all the vulnerability code, so Metasploit has a very powerful feature that allows users to develop their own vulnerability module, s2-045 exploit module Metasploit though not yet integrated , But the network has a corresponding penetration module, and these modules may be written in a variety of languages, such as perl, python, etc., Metasploit support a variety of languages prepared by the module transplanted to its framework, through this mechanism can be A variety of existing modules are migrated to Metasploit-compatible infiltration modules.
We first download the S2-045 vulnerability in github exploit the ruby script, which has been tested by the author and can be used directly. Download: https://github.com/rapid7/metasploit-framework/pull/8072, save as struts2_code_exec_jakarta.rb, and then put it on the KALI system /usr/share/metasploit-framework/modules/exploits/multi/http/ directory.
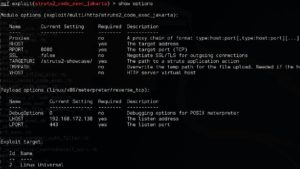
Now we go to MSF search struts2 can be found below the script, as shown below.

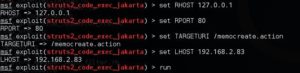
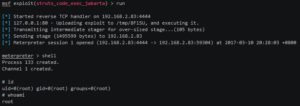
Start Metasploit, use the vulnerability module, and set the corresponding payload, here because my virtual machine is linux, so here with the Linux payload, then look at the specific parameters of the module, as shown below.
![]()