
Overview
Our research team has uncovered a new Zero-Day attack for taking full control over major antiviruses and next-generation antiviruses. Instead of hiding and running away from the antivirus, attackers can now directly assault and hijack control over the antivirus.
The attack begins when the attacker injects code into the antivirus by exploiting a new Zero-Day vulnerability. Once inside, the attacker can fully control the antivirus. We named this attack DoubleAgent, as it turns your antivirus security agent into a malicious agent, giving an illusion that the antivirus protects you while actually it is abused in order to attack you.
DoubleAgent exploits a 15 year old vulnerability which works on all versions of Microsoft Windows, starting from Windows XP right up to the latest release of Windows 10. The sad, but plain fact is that the vulnerability is yet to be patched by most of the antivirus vendors and could be used in the wild to attack almost any organization that uses an antivirus. Once the attacker has gained control of the antivirus, he may command it to perform malicious operations on behalf of the attacker. Because the antivirus is considered a trusted entity, any malicious operation done by it would be considered legitimate, giving the attacker the ability to bypass all the security products in the organization.
The attack has been tested and proven on all the major antiviruses as well as of all versions of Microsoft Windows. The attack was reported to all the major vendors which approved the vulnerability and are currently working on finding a solution and releasing a patch.
How Does DoubleAgent Work?
DoubleAgent exploits a legitimate tool of Windows called Microsoft Application Verifier which is a tool included in all versions of Microsoft Windows and is used as a runtime verification tool in order to discover and fix bugs in applications. Our researchers discovered an undocumented ability of Application Verifier that gives an attacker the ability to replace the standard verifier with his own custom verifier. An attacker can use this ability in order to inject a custom verifier into any application. Once the custom verifier has been injected, the attacker now has full control over the application.
Application Verifier was created in order to strengthen application security by discovering and fixing bugs, and ironically DoubleAgent uses this feature in order to perform malicious operations.
Vulnerable Antiviruses
The list of vendors that have been tested and found to be vulnerable to DoubleAgent.
The tests were done on the latest version of the vendor on Windows 10 x64 using our POC code.
Avast (CVE-2017-5567)
AVG (CVE-2017-5566)
Avira (CVE-2017-6417)
Bitdefender (CVE-2017-6186)
Trend Micro (CVE-2017-5565)
Comodo
ESET
F-Secure
Kaspersky
Malwarebytes
McAfee
Panda
Quick Heal
Norton
Antivirus Attack Vectors
During a normal cyber attack, the attacker would invest a lot of effort hiding and running away from the antivirus. By using DoubleAgent, the attack can take full control over the antivirus and do as he wish without the fear of being caught or blocked. He could:
1. Turn the Antivirus into a malware – Perform malicious operations on behalf of the attacker. Because the antivirus is considered a trusted entity, any malicious operation done by it would be considered legitimate, giving the attacker the ability to bypass all the security products in the organization.
2. Modify the Antivirus internal behaviour – Changing the antivirus whitelists/blacklists, internal logic and even installing backdoors. The antivirus would still appear to work normally but would actually be completely useless, giving the attacker the ability to execute malware that would normally be blocked without any interference.
3. Abusing the Antivirus trusted nature – The antivirus is considered one of the most trusted entities in an organization. The attacker can use the antivirus to perform operations that would normally raise “red flags” like exfiltrating data, C&C communication, lateral movement, stealing and decrypting sensitive data, etc. All of these operations would seem legit because they are done by the antivirus.
4. Destroy the Machine – The antivirus has complete power over the machine, which can allow it to easily encrypt all your files or even format your hard drives.
5. Denial of Service – An antivirus software is responsible for signing software to act maliciously based on a set of heuristic rules. This means that the attacker can sign a totally legit and critical software such as browser applications, document viewers, or even some key components that are deep within the operating system. Once the signature has spread across the organization, it would then cause a total denial of services for the entire company. Once an antivirus decides a file is malicious, it would create a signature for it and share it globally around the world. Because the attacker controls the antivirus, he may sign totally legit and critical applications such as browsers, document viewers, or even some key components that are deep within the operating system. Once the new signature has spread across the organization, all the other instances of the antivirus would remove/delete the critical application causing total denial of services for the entire organization.
Additional Attack Vectors
Generic Persistency (auto-run) Technique
Persistence is any action that gives an attacker a persistent presence on that system. Attackers will often need to maintain access to systems through interruptions such as system restarts.
Today there are just a few known persistence mechanisms.
AVs and NGAV, are constantly monitoring for these techniques and trying to detect malicious process that trying to use any of those techniques. DoubleAgent can continue injecting code even after reboot making it a perfect persistency technique to “survive” reboots-updates-reinstalls-patches-etc.
Once a persistence technique is well-known, security products update their signatures accordingly. So once the persistence is known, it can be detected and mitigated by the security products.Being a new persistence technique, DoubleAgent bypasses AV, NGAV and other endpoint solutions, and giving an attacker ability to perform his attack undetected with no time limit.
Generic Code Injection Technique
This technique can also be used as a new way of injecting code into any application and as a result, be able to bypass current security solutions that attempt to prevent such injections and in the process, adding malicious code into legitimate processes. Under the disguise of the legal operations, an attacker is then able to steal data, encrypt data or even take part in other activities without interruptions since no security solution is capable of detecting this kind of code injection. As such, the attacker can be able to feed malicious code into your system and by doing so, be in a position to steal your information from under your nose without any detection by your security products.
Since the DoubleAgent technique uses legitimate operating system mechanism to inject its code, it can’t be patched and this injection technique will live forever. So there is no notion of a patch.
Mitigation
Microsoft has provided a new design concept for antivirus vendors called Protected Processes. The new concept is specially designed for antivirus services. Antivirus processes can be created as “Protected Processes” and the protected process infrastructure only allows trusted, signed code to load and has built-in defense against code injection attacks. This means that even if an attacker found a new Zero-Day technique for injecting code, it could not be used against the antivirus as its code is not signed. Currently no antivirus (except Windows Defender) has implemented this design. Even though Microsoft made this design available more than 3 years ago. It’s important to note, that even when the antivirus vendors would block the registration attempts, the code injection technique and the persistency technique would live forever since it’s legitimate part of the OS.
Summary
Attackers are always evolving and finding new Zero-Day attacks.
We need to make more efforts to detect and prevent these attacks, and stop blindly trusting traditional security solutions, that as shown here, are not only ineffective against Zero-Days but also open new opportunities for the attacker to create complicated and deadly attacks.
Appendix A – Taking Full Control Over Norton Antivirus POC
We’ve created a full proof-of-concept demonstration taking over the latest version of Symantec Norton antivirus, in that demo we’ve injected a code into Norton, a mission that itself considered very difficult as Norton, similar to any other antivirus makes tons of checking and use many self-protection techniques to make sure it won’t happen, the code changes all Norton’s user interface and give the attacker an ability to perform malicious operations under Norton’s process, such as converting it to a ransomware and encrypting files.
The full demonstration can be found in this video.
Here is the original window of the antivirus, that shows that everything is protected:
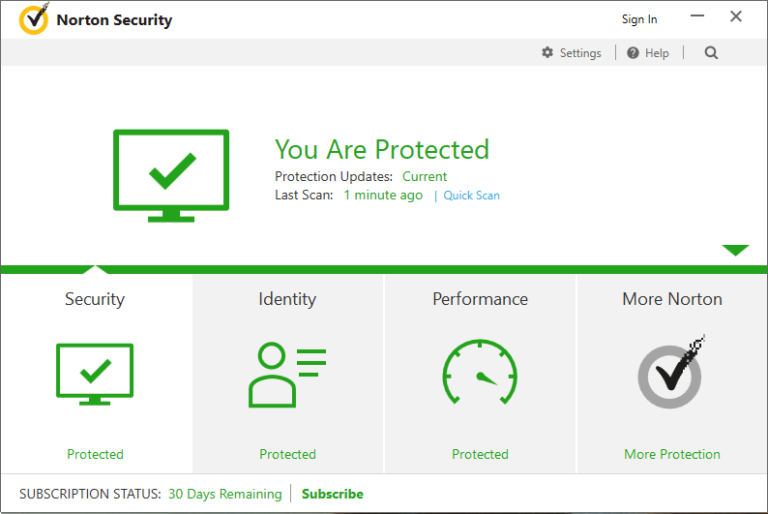
And below is the modified version, after DoubleAgent was injected into it and made its malicious modifications:
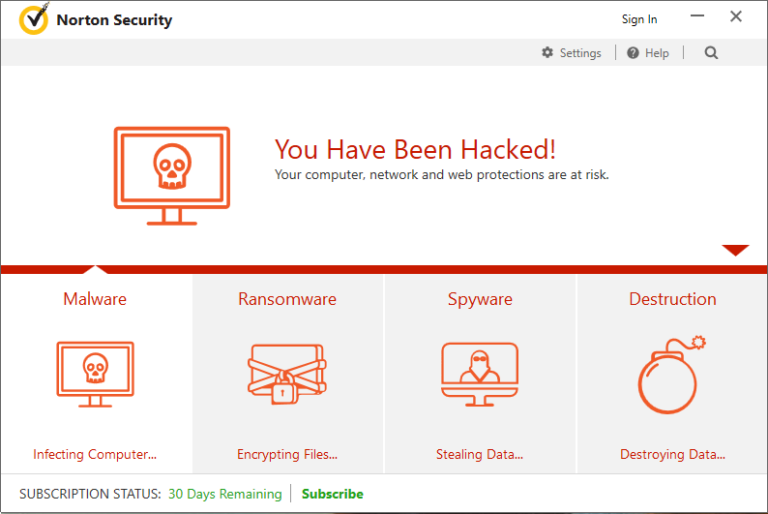
Update
-To clarify, of course we haven’t discovered the existence of Application Verifier, it’s part of the OS so users can use it. Application Verifier as a hooking technique was discussed long ago as early as 2011. What we discovered and focused about was that AVRF can be used for:
1. Generic code injection technique that is undetected by AV.
2. Generic persistence technique that is also undetected by AV.
3. And most importantly, injecting code directly into the AV while bypassing its self-protection techniques.
None of these points where discussed in previous articles. We believe these points are a significant tool that can be used by attackers to help bypass and abuse antivirus software.
– You do need a privileged account to run DoubleAgent as DoubleAgent is designed as a post-breach attack. Even after a computer is breached, and attacker still needs to hide from the AV, spread its code, maintain persistence and find ways to exfiltratestealencrypt data without being caught. DoubleAgent gives the attacker the ability to control the AV and perform all the operations above without being detected, while keeping the illusion that the AV is working normally.
– ESET AV do implement “Protected Processes”, however, not over all process so they are still vulnerable.
Disclaimer:
These materials are for educational and research purposes only. Do not attempt to violate the law with anything contained here.
Original source
![]()
