
A simple phishing toolkit created by Jordan Wright. That is a framework that allows the easy management of phishing campaigns. It even handles the malicious web pages that you create. This is available for all OS types and you can grab this tool from github.com.
Tutorial
Once you have the server set up and you can simply download the GoPhish release by typing:
wget https://github.com/gophish/gophish/releases/download/v0.2.0/gophish-v0.2-linux-64bit.zip
Once that is downloaded we can then unzip the folder
unzip gophish-v0.2-linux-64bit.zip
then we can cd into that folder. Once in that folder we then need to make the gophish file executable we can do this by typing:
chmod +x gophish
once this is done we then need to edit our config.json file. and edit the listen_url to
"listen_url" : "0.0.0.0:3333",
we do this to allow gophish to listen on all interfaces. Now we can go head and start GoPhish by typing:
./gophish
GoPhish should now be started and if you look in the terminal that you started GoPhish you should see that two servers have been created. 1st being the admin interface which allows us to manage our phishing campaigns and the 2nd server started acts as a web server to create malicious clones. You can proceed to log in by using the credentials of admin:gophish
Now that we have logged into we are presented with the dashboard. From here we can navigate to the Sending Profiles tab on the left-hand side of the site and click New Profile. We then proceed to fill out the form presented to us.
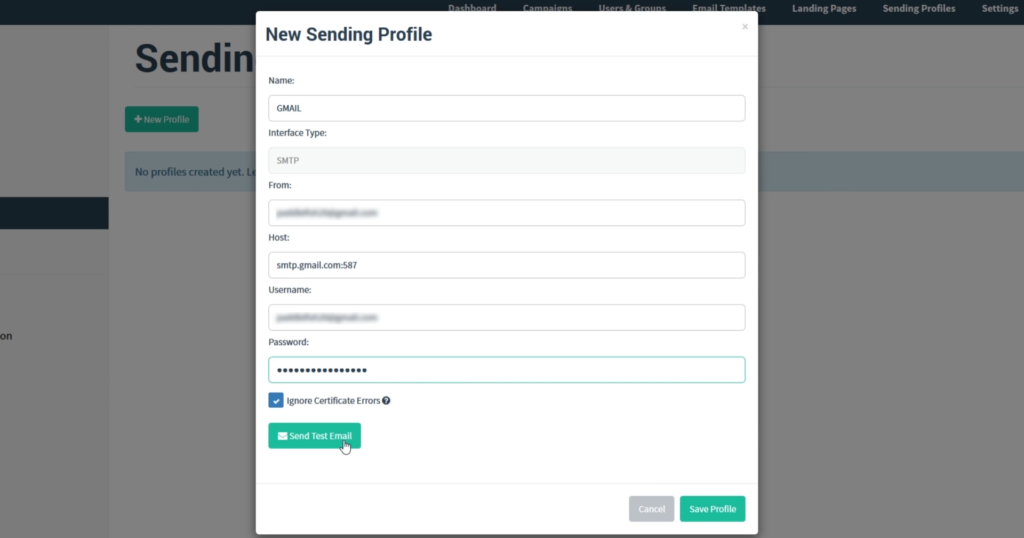
The details that you enter will be from an email address that you already have created, with the username and password also being the same. We can check to make sure that all the details have been entered in correctly and that we are able to send emails. we simply click Send Test Email.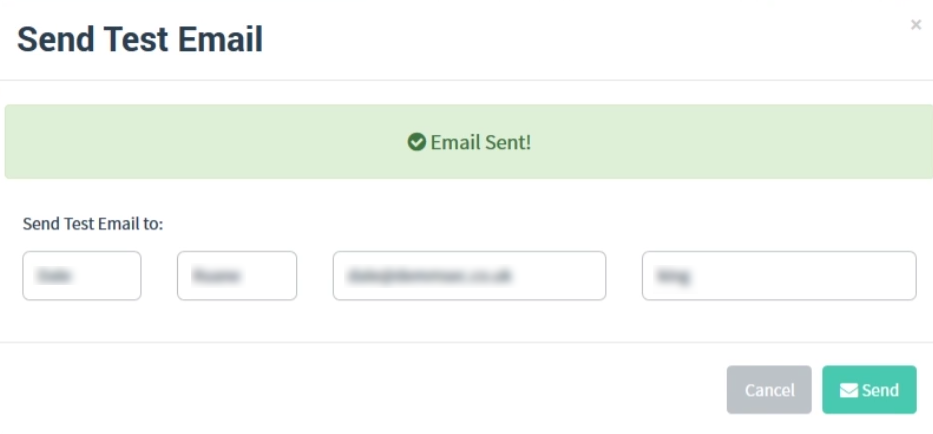
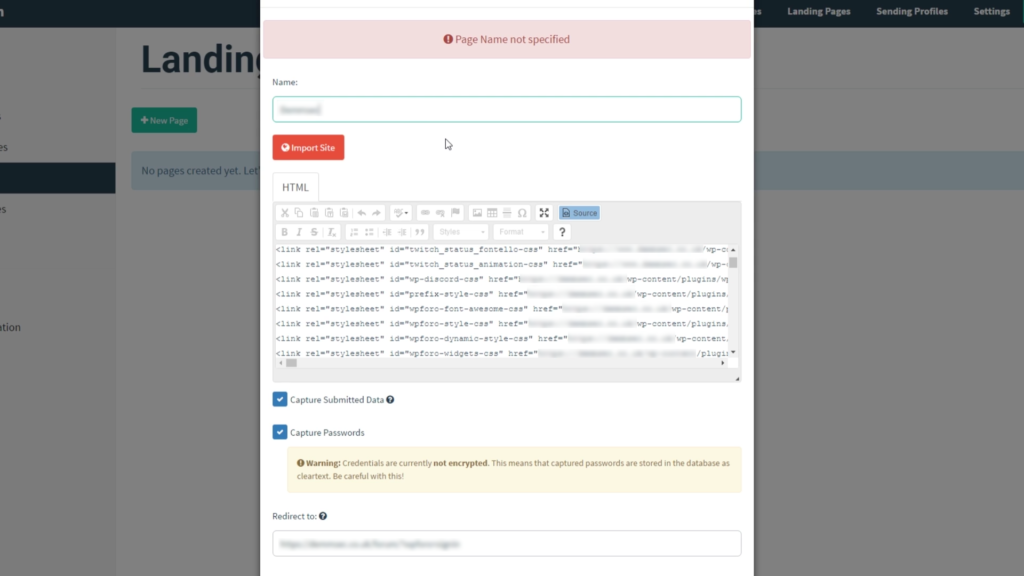
We can then move on to the Landing Page. Just like before click New Page and in the form entering the required details. Choosing a Page Name that you can remember, later on, we recommend using the same name as whatever website it is you are going to clone. Then we are able to import the site that we want to clone by clicking import site. With the new popup that appears, we simply add the URL of the site we want to clone. Once that is done we select Capture Submitted Data and Capture Passwords. We can then add a Redirect to the site, in this case, we use who-ami’s login page.
Moving on to Email Templates, we again name the template LinkedIn. We can then import an email for this we used and old email that dale had a LinkedIn request from myself. In thunderbird, we are able to view the email source and copy this into the Email Content on GoPhish. We also have the Change Links to Point to Landing Page, which will allow any link in the email to automatically send us to the phishing clone. We can then save this template.
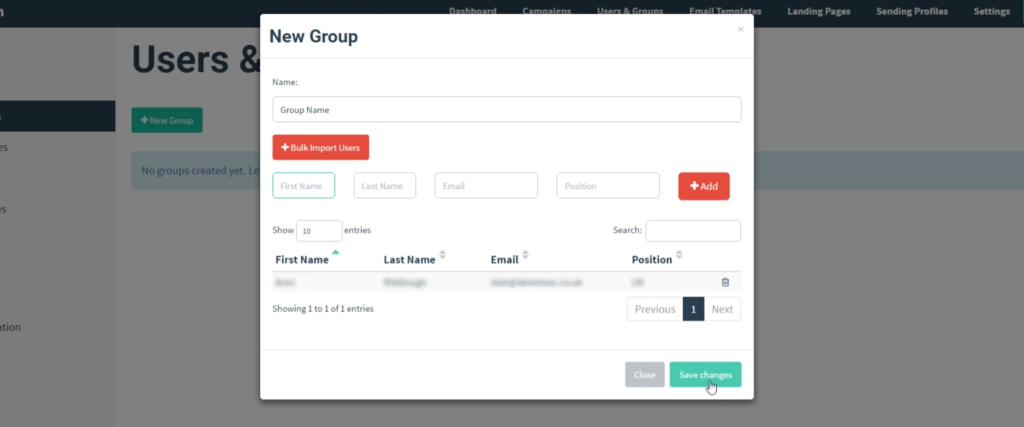
We finally then add Users and Groups, to which we add the Group Name. Then the first and last name, an email and their position and add this to the list. We can also bulk import users into the group.
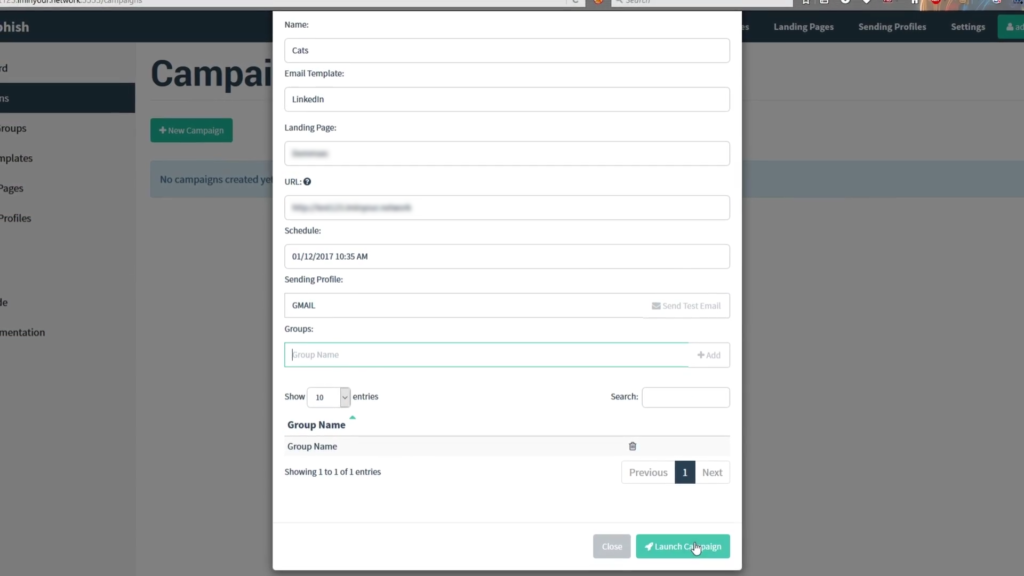
OK I lied not exactly the last step, however, this step is actually bringing everything that we have already done into one final element. We need to enter all the information we previously entered in our other steps along with naming the campaign and adding the URL of the site to which will capture the data. In this case, we have set-up and bought a domain of test123.network we can the schedule when we want the email to be sent. We use the Sending Profile and Groups that we created earlier and then we can launch the campaign.
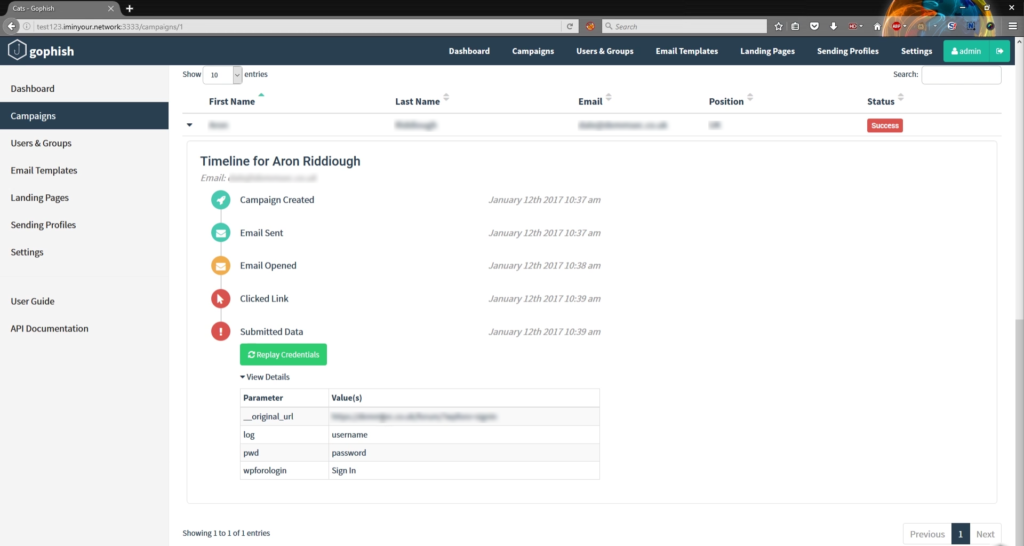
Now that is done it will have started to send out emails. We now see the active campaign in our dashboard and we wait for the email to be received. Within the dashboard, we can also see a timeline of the campaign, this is pretty cool as it will show you when the campaign was created, the email sent, the email opened if the link was clicked and if there was any data submitted. So a pretty decent audit trail. The submitted data allows us to see what data was entered, but yet another cool feature is that we can replay the credentials and this allows us to automatically login to that site with them credentials!
![]()
